Groups
This page gives an overview of groups in Databricks. For how to manage groups, see Manage groups.
Groups simplify identity management by making it easier to assign access to workspaces, data, and other securable objects. All Databricks identities can be assigned as members of groups.
This page assumes your workspace has identity federation enabled, which is the default for most workspaces. For information about legacy workspaces without identity federation, see Legacy workspaces without identity federation.
Group sources
Databricks groups are classified into four categories based on their source, which is shown in the Source column of the groups list
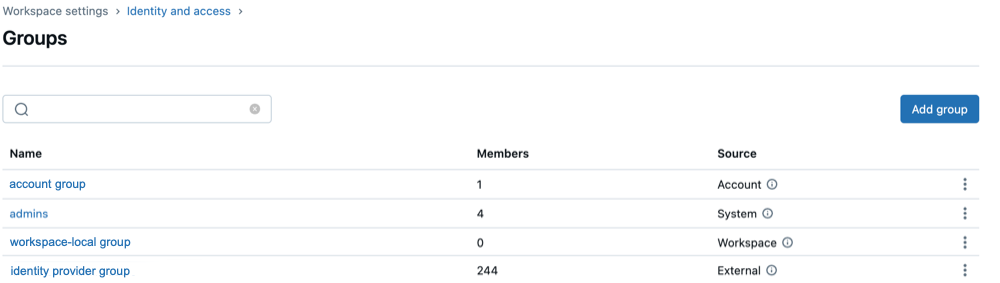
Source | Description |
|---|---|
Account | Can be granted access to data in a Unity Catalog metastore, assigned roles on service principals and groups, and permissions to workspaces. These are the primary groups for managing access across the Databricks account. |
External | Created in Databricks from your identity provider. These groups stay in sync with your IdP (such as Microsoft Entra ID). External groups are also considered account groups. |
System | Created and maintained by Databricks. Each account includes an |
Workspace | Known as workspace-local groups, these are legacy groups that used only within the workspace in which they were created. They cannot be assigned to other workspaces, granted access to Unity Catalog data, or assigned account-level roles. Databricks recommends converting workspace-local groups to account groups for broader functionality. |
Who can manage groups?
To create groups in Databricks, you must be either:
- An account admin
- A workspace admin
To manage groups in Databricks, you must have the group manager role (Public Preview) on a group. This role allows you to:
- Manage group membership
- Delete groups
- Assign the group manager role to other users
By default:
- Account admins automatically have the group manager role for all groups.
- Workspace admins automatically have the group manager role on groups that they create.
Group manager roles can be configured by:
- Account admins, using the account console
- Workspace admins, using the workspace admin settings page
- Non-admin group managers, using the Accounts Access Control API
Workspace admins can also create and manage legacy workspace-local groups.
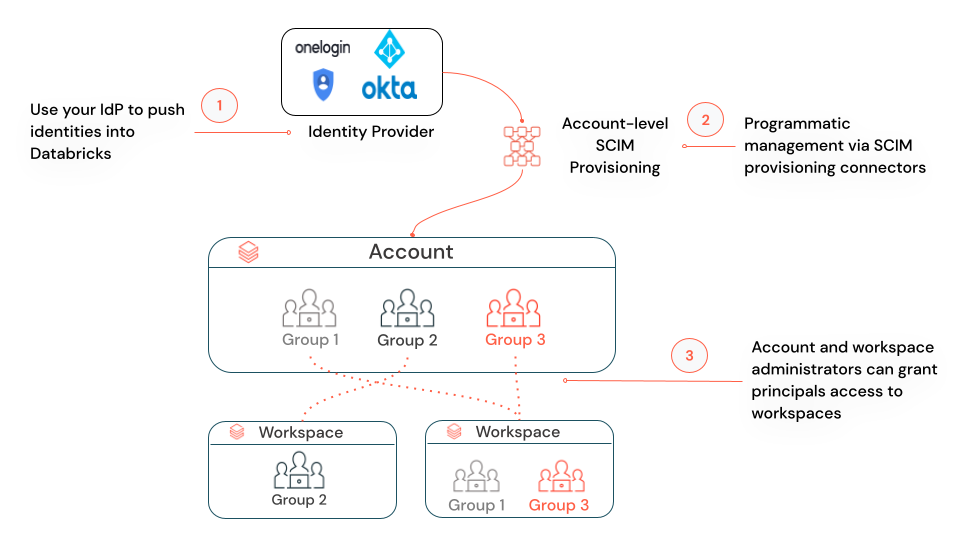
Sync groups to your Databricks account from an identity provider
Databricks recommends syncing groups from an identity provider to your Databricks account using a SCIM provisioning connector. For instructions, see Sync users and groups to your Databricks account.