Configure SCIM provisioning for OneLogin
This article describes how to set up Databricks provisioning using Onelogin.
For a user to log in using OneLogin, you must configure single sign-on from OneLogin to Databricks. See Configure SSO in Databricks.
Requirements
- Your Databricks account must have the Premium plan or above.
- You must be Databricks account admin.
- Your OneLogin account must support provisioning.
- You must be a Super User or Account Owner for your OneLogin account.
- Databricks recommends that you read the OneLogin article, What is User Provisioning and Deprovisioning?.
- Configure single sign-on for users to log in to Databricks using OneLogin. See Configure SSO in Databricks.
Set up account-level SCIM provisioning using OneLogin
This section describes how to configure an OneLogin SCIM connector to provision users and groups to your account.
Get the SCIM token and account SCIM URL in Databricks
- As an account admin, log in to the Databricks account console.
-
Click Security.
-
Click User provisioning.
-
Click Set up user provisioning.
Copy the SCIM token and the Account SCIM URL. You will use these to configure your connector in OneLogin.
-
The SCIM token is restricted to the Account SCIM API /api/2.1/accounts/{account_id}/scim/v2/ and cannot be used to authenticate to other Databricks REST APIs.
Configure the OneLogin SCIM provisioning app
-
Log in to OneLogin as a Super User or Account Owner, and launch the OneLogin admin console.
-
Go to Applications and click Add App.
-
Search for and select SCIM Provisioner with SAML (SCIM v2 Core).
-
Click Save. New configuration tabs appear at the left.
-
Click Configuration.
-
In Databricks subdomain, enter the Account SCIM URL.
-
In the SCIM Bearer Token field, enter the Databricks personal access token.
-
Under API Connection, click Enable. The application authenticates to Databricks.
-
Go to Provisioning to enable and configure provisioning.
-
Under Workflow, select Enable provisioning.
-
Configure whether to require admin approval to create, delete, or update a user.
noteDatabricks recommends that you enable admin approval for all operations as an initial safeguard, so that you don't trigger automatic provisioning for your users before setup and testing have been completed. After you have tested and verified that provisioning is working as expected, you can configure these settings to override admin approval.
-
Configure the behavior in Databricks when a user is deleted from OneLogin:
- Do nothing does not modify the user in Databricks.
- Suspend disables the user in Databricks. The user can't log in, but the user's resources are not modified. This is reversible.
- Delete deletes the user in Databricks and archives the user's resources. This is not reversible.
-
Configure the behavior in Databricks when a user is suspended in OneLogin.
- Do nothing does not modify the user in Databricks.
- Suspend disables the user in Databricks. The user can't log in, but the user's resources are not modified. This is reversible.
-
Under Entitlements, click Refresh. In OneLogin, groups are called entitlements. This imports groups from Databricks into OneLogin. Importing OneLogin entitlements into Databricks is not supported.
-
-
Click Save.
Continue to Use OneLogin to manage users and groups in Databricks to provision users and groups in your Databricks account.
Use OneLogin to manage users and groups in Databricks
This section describes how to use OneLogin to manage users and groups the Databricks account.
Assign groups to Databricks workspace users
You must create Databricks groups in Databricks and create mappings to keep them in sync with OneLogin fields. You cannot add groups to Databricks using OneLogin.
- In OneLogin, go to the Parameters tab.
- Under Optional Parameters, click on Groups.
- Verify that all of the group names were successfully imported from Databricks to the Values field when you clicked Refresh on the Provisioning tab (above), and select the Include in User provisioning flag.
- Click Save.
Once you have configured your attribute mapping, you can assign groups to Databricks users when you provision them. To assign Group values, you can manually select them on the user login record for the OneLogin SCIM provisioning app. On the Users tab of the OneLogin SCIM provisioning app, select the user to edit.
You can also use OneLogin rules (mappings) to assign users to Databricks groups automatically, based on another OneLogin attribute, such as OneLogin Role. For example, to place all users who are in the OneLogin Role “Finance” in the Databricks “finance” group, you can go to the Rules tab in your OneLogin SCIM provisioning app and create a New Rule with the condition Roles – include – Finance and the action Set Groups in Databricks to – finance, as in this screenshot:
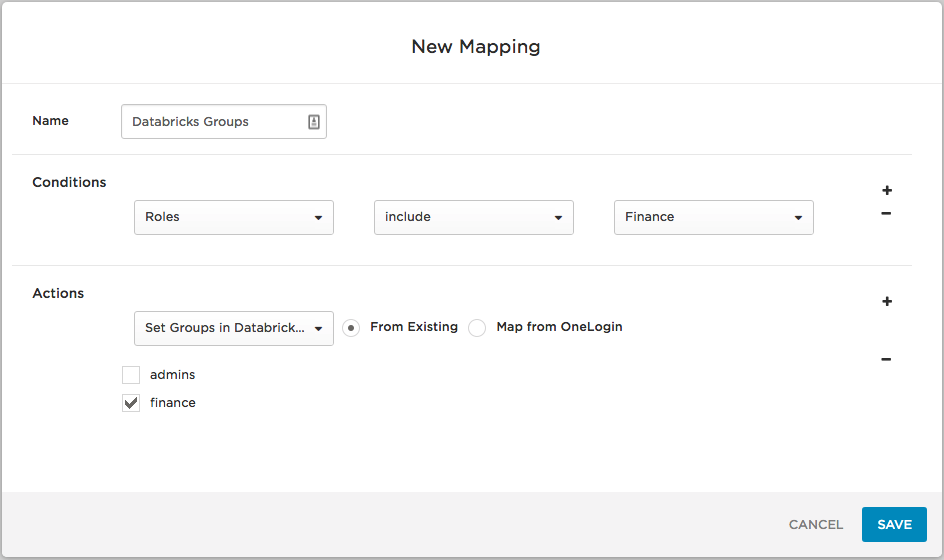
Now, whenever you add a user to the OneLogin “Finance” role and the OneLogin SCIM provisioning app, the user will be assigned the “finance” group in Databricks when you reapply entitlement mappings.
Remove or update group assignments
To remove or update group assignments go to the Users tab in the OneLogin SCIM provisioning app and select the user to edit. Remove or override the current selection in the group field, custom IAM role field, or custom entitlement field.
If you have set up rules to assign groups to the user based on a OneLogin attribute, such as OneLogin Role, remove that attribute from the user (for example, remove the user from the OneLogin Role). You can also change the rule that assigns the group, IAM role, or entitlement to users in that OneLogin role.
Trigger a sync
You can manually trigger a sync of OneLogin users with Databricks users by going to the OneLogin SCIM provisioning app and selecting MORE ACTIONS -> Sync logins. If a user is assigned to the app, the user will be added to your Databricks account. However, the reverse is not true: a user created in the Databricks account will not be added to the OneLogin SCIM provisioning app.
To manually sync users from the Databricks account to OneLogin, create a user in OneLogin with the same username and email address as the user in the Databricks account, and then assign the user to the app in OneLogin.
Delete users
When you delete users in OneLogin, OneLogin deactivates them from the Databricks account.
Do not remove the administrator who configured the OneLogin SCIM provisioning app from Databricks or from the admins group. Otherwise, the SCIM integration cannot authenticate to Databricks.
You can deactivated a user in multiple ways:
- Delete or suspend the user from OneLogin.
- Remove the user from the app manually by going to the Users tab in the OneLogin SCIM provisioning app, selecting the user, and clicking the Delete button.
- If you have set up rules to assign the user to the app based on a OneLogin attribute, such as OneLogin Role, remove that attribute from the user (for example, remove the user from the OneLogin Role). You can also remove then Databricks app from a OneLogin Role that the user is assigned to (this deprovisions Databricks for all users in the role).
If you remove a user from the account-level SCIM application, that user is deactivated from the account and from their workspaces, regardless of whether or not identity federation has been enabled.
If you delete a OneLogin-managed user directly in Databricks, the user will remain active in the OneLogin SCIM provisioning app. When you try to delete the user from the OneLogin SCIM provisioning app, the attempt will fail, because the user is already deleted in Databricks.
Troubleshooting and tips
- Users who existed in Databricks prior to provisioning setup:
- Are automatically linked to a OneLogin user if they already exist in OneLogin and are matched based on email address (username).
- Can be manually linked to an existing user or created as a new user in OneLogin if they are not automatically matched.
- User permissions that are that are assigned individually and duplicated through membership in a group remain after the group membership is removed for the user.
- You must create Databricks groups in Databricks; you cannot add groups using OneLogin.
- You cannot update Databricks usernames and email addresses.