Add resources to a Databricks app
Your Databricks apps can integrate with various Databricks platform features, such as Databricks SQL for querying data, Lakeflow Jobs for data ingestion and processing, Mosaic AI Model Serving to access generative AI models, and Databricks secrets for managing sensitive information. In the context of apps, these platform features are referred to as resources.
Why use resources?
To keep apps portable and secure, avoid hardcoding resource IDs. For example, instead of embedding a fixed SQL warehouse ID in your app code, configure the SQL warehouse as a resource through the Databricks Apps UI.
Using Databricks Apps resources instead of direct API calls has several benefits:
- Automatically manages credentials and permissions, which eliminates manual token handling in your code.
- Handles resource paths, endpoints, and connection details automatically.
- Provides secure, managed access instead of requiring self-managed credentials for direct API calls.
- Keeps apps portable between environments without code changes.
Supported resource types
The following table lists all resource types that you can add to your Databricks app:
Resource type | Description | Default resource key | Available permissions |
|---|---|---|---|
AI-powered analytics interface for natural language queries |
|
| |
Unity Catalog database for data storage and querying |
|
| |
Data ingestion and processing workflows |
|
| |
Machine learning experiment tracking and model lifecycle management |
|
| |
Machine learning model deployment for inference requests |
|
| |
Secure storage for sensitive values like API keys and tokens |
|
| |
Compute resources for running SQL queries |
|
| |
Managed connections to external data sources |
|
| |
Registered SQL and Python functions in Unity Catalog |
|
| |
File storage in Unity Catalog for app artifacts and data |
|
| |
Semantic search and similarity-based retrieval from vector embeddings |
|
|
Prerequisites
To add a resource to an app, the following conditions must be met:
- The resource must exist.
- The user adding the resource must have the
Can managepermission on the resource and the app.
Apps run with least privilege and rely on existing resources within the Databricks platform. When deployed, the app’s service principal accesses these resources and must have the necessary permissions, such as table-level access for SQL queries or read access to secrets. See Configure authorization in a Databricks app.
Configure resources for your app
Resources allow your app to securely connect to services that it depends on, without hardcoding sensitive or environment-specific values.
Add resources directly in the Databricks Apps UI when you create or edit an app.
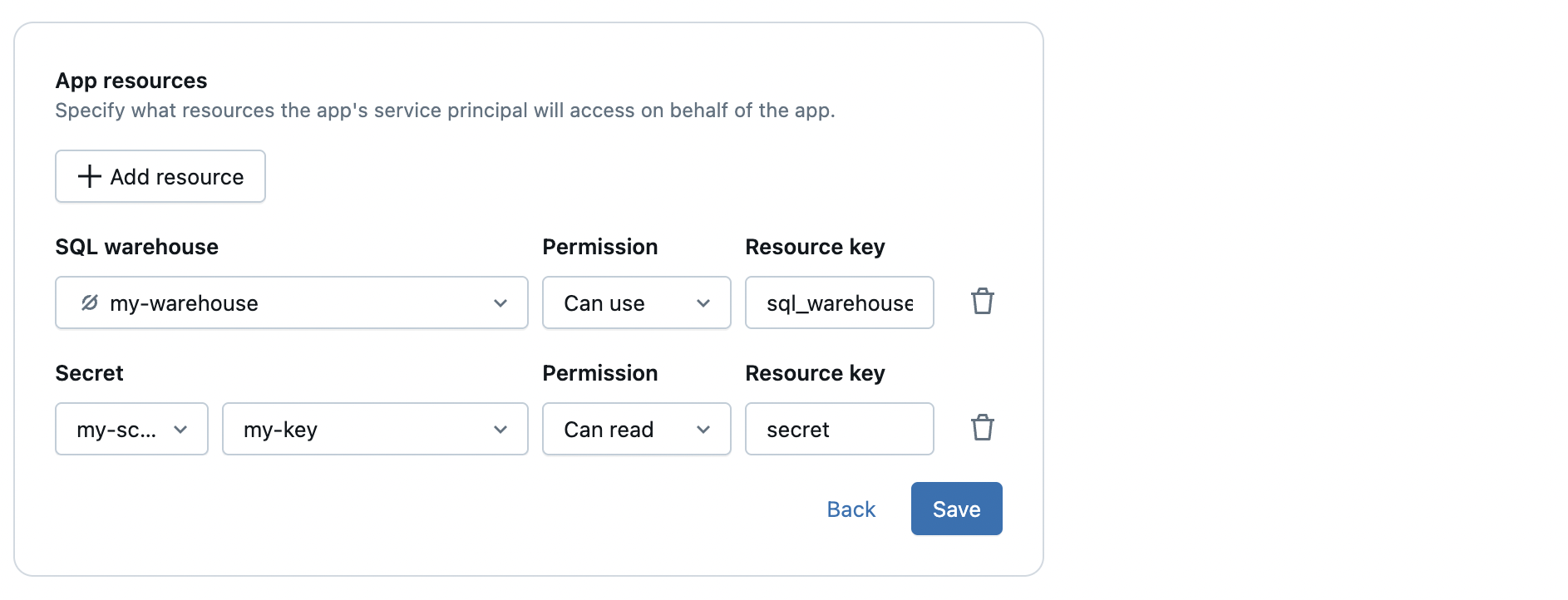
- When you create or edit an app, navigate to the Configure step.
- In the App resources section, click + Add resource.
- Select the resource type you want to add.
- Set the permissions for the app service principal on the resource.
- Assign a key to the resource, and reference that key in your
app.yamlfile.
Manage app access to resources
Each app has a dedicated service principal. Follow these best practices to manage access securely.
- Use the app's service principal for authentication. Never hardcode personal access tokens (PATs) in your code. Access credentials are automatically injected as environment variables:
DATABRICKS_CLIENT_IDDATABRICKS_CLIENT_SECRET
- Don't share service principal credentials between apps or across users. Each app should use its own dedicated credentials for isolation and security.
- Apply least privilege access. Grant only the minimum required permissions to the app's service principal. For example:
- Grant
CAN USEon a SQL warehouse if the app only needs to run queries. - Grant
CAN QUERYon a serving endpoint if the app only sends inference requests. - Grant
SELECTorMODIFYon Unity Catalog tables based on the app’s data access needs.
- Grant
Next steps
After you add resources to your app, reference these resources in the env section of your app configuration using the valueFrom field. For instructions, see Define environment variables in a Databricks app.