AI/BI administration guide
This page describes the account and workspace-level administrative controls that can be applied to AI/BI products.
Manage dashboard and Genie access
Users are granted entitlements at the workspace level that control how they interact with the Databricks workspace. See Manage entitlements for details about each access type.
Dashboards and Genie spaces can be securely shared with the following user types:
- Workspace users: Permissions are scoped to the workspace where they are a member. To access multiple workspaces, they must be added to each workspace individually. Their access is controlled by entitlements that determine how they interact with data assets.
- With the Databricks SQL access entitlement: Users can create new dashboards and Genie spaces. Access can be granted to view, edit, and manage draft and published dashboards. Access can be granted to compute and Unity Catalog governed data.
- With the Consumer access entitlement: Users can be granted access to published dashboards. Access can be granted to compute and Unity Catalog governed data. To learn more, see What is consumer access?.
- Account users: Can be granted access to published dashboards with shared data permissions. Account users must be registered to your Databricks account, but they do not need access to any additional resources or to be added to a workspace. Account users can be assigned as recipients for dashboards or Genie spaces across any workspace in the account. See [_](/dashboards/share/share.md to learn more about published dashboards and shared data permissions.
To change the default workspace access for new users to Consumer access, see Change default workspace access to consumer access. For more information about entitlements, see Manage entitlements.
Capabilities by access type
The following table summarizes the capabilities associated with each access type:
Capability | Account member access | Consumer access | Databricks SQL access |
|---|---|---|---|
View/run dashboards | ✓ | ✓ | ✓ |
View/run Genie spaces | ✓ | ✓ | |
Enforce row- and column-level security on view | ✓ | ✓ | |
Query SQL warehouses using BI tools | ✓ | ✓ | |
Access Unity Catalog-governed data through third-party BI tools | ✓ | ||
Read/write AI/BI dashboards | ✓ | ||
Read/write Genie spaces | ✓ |
Account users can view dashboards published with shared or individual data permissions. However, account users cannot access data from workspace-bound securables, such as workspace-bound catalogs.
Network considerations
If IP access lists are configured, dashboards are only accessible if users access them from within the approved IP range, such as when using a VPN. This applies to all users, regardless of whether they are assigned to a workspace. For more information on configuring access, see Manage IP access lists.
User and group management
All users registered with Databricks belong to your Databricks account. Registering a user in a Databricks account establishes a verifiable identity that Databricks can use for authentication when that user views a shared dashboard or Genie space. Organizing individual users into groups can make sharing easier for authors and editors. For example, an author can share with a single, named group instead of sharing with each user in the account.
Users must have the appropriate data and compute privileges to interact with a Genie space, which can only be granted to workspace users.
Dashboard account-level sharing supports email and one-time passcode authentication, as well as unified login with single sign-on (SSO). If a dashboard is shared when the recipient uses one-time passcode login and then the account is later configured for SSO with unified login, account admins should verify that dashboard recipients are allowed to access the Databricks account using their identity provider configuration. Users who aren't allowed to log in using SSO can no longer access dashboards that were previously shared with them.
Users and groups can have access to zero, one, or multiple workspaces. Authors can add users and groups to a People with access list to assign specific permissions, as with other workspace objects, when sharing a dashboard or Genie space.
For dashboards, they can configure Sharing settings with one of the following options:
- Only people with access can view
- Anyone in my account can view
If a dashboard is published with shared data permissions and shared with a specific user, group, or all users in the account, those users can access it regardless of whether they have access to the originating workspace.
The following image shows the relationship between users and groups at the workspace and account levels.
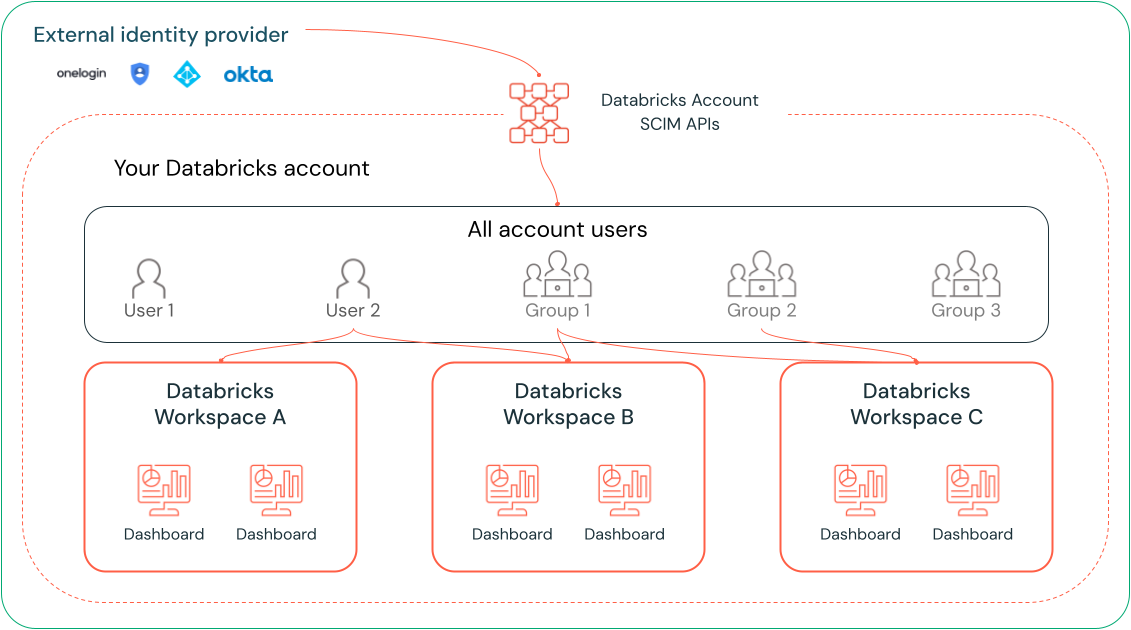
Databricks recommends that account admins use account-level SCIM provisioning to sync all users and groups automatically from your identity provider to your Databricks account. You can also manually register these users and groups as you set up identities in your Databricks account. This approach allows them to be included as eligible recipients before an author attempts to share a dashboard. See Enable all identity provider users to access Databricks.
No additional configuration is required beyond account registration. Users do not need to be assigned to a workspace or given access to compute resources.
Manage dashboard embedding
Users can securely embed dashboards in external websites and applications. Each embedding option requires a workspace admin to configure settings and permissions. To learn how to manage embedding settings, see Manage dashboard embedding.
Workspace admin subscription controls
Workspace admins can prevent users from distributing dashboards using subscriptions. Changing this setting prevents all users from adding email subscribers to scheduled dashboards. Dashboard editors cannot add subscribers, and dashboard viewers do not have the option to subscribe to a scheduled dashboard.
To prevent sharing email updates:
- Click your username in the top bar of the Databricks workspace and select Settings.
- In the Settings sidebar, click Notifications.
- Turn the Enable dashboard email subscriptions option off.
If this setting is off, existing subscriptions are paused, and no one can modify existing subscription lists. If this setting is turned back on, subscriptions resume using the existing list.
Configure Slack or Microsoft Teams notifications
Dashboard editors can add Slack and Microsoft Teams channels as subscribers to a schedule. Before users can subscribe Slack or Microsoft Teams channels to dashboard schedules, configure Slack or Microsoft Teams notification destinations as a workspace admin.
Slack and Teams subscriptions deliver dashboard snapshots that include:
- A PNG image snapshot of the dashboard visible directly in the channel
- A direct link to open the dashboard in Databricks
- A PDF snapshot attachment in the message thread
For step-by-step instructions on creating an app, configuring OAuth permissions, and setting up notification destinations for dashboard subscriptions, see Configure Slack notifications for Slack destinations, and Configure Microsoft Teams notifications for Microsoft Teams destinations.
Download controls
Workspace admins can adjust their security settings to prevent users from downloading dashboard and Genie space results using the following steps:
- Click your username in the top bar of the Databricks workspace and select Settings.
- In the Settings sidebar, click Security.
- Turn the SQL results download option off.
Transfer ownership of a dashboard
Workspace admins can transfer ownership of a dashboard to a different user.
- Go to the list of dashboards. Click a dashboard name to edit it.
- Click Share.
- Click the
icon at the top-right of the Sharing dialog.
- Start typing a username to search for and select the new owner.
- Click Confirm.
The new owner appears in the Sharing dialog with CAN MANAGE permissions. To view dashboards listed by owner, go to the list of available dashboards by clicking Dashboards.
Monitor AI/BI activity
Due to an outage, some dashboard audit logs might be missing for the period October 16, 2025 – November 19, 2025.
Admins can monitor the activity on dashboards and Genie spaces using audit logs. See AI/BI dashboard events and AI/BI Genie events. For code examples that demonstrate how to access audit log information to answer common questions, see Monitor Genie spaces usage with audit logs and alerts.