Configure DNS for AWS inbound PrivateLink
Configure DNS to route user requests through your private network when using inbound PrivateLink for Databricks workspaces. This page covers DNS configuration patterns and step-by-step setup instructions. Although you can configure DNS for AWS PrivateLink in multiple ways, this page defaults to a recommended approach that works for most deployments.
Back-end PrivateLink endpoints automatically use AWS DNS resolution when you enable the Enable DNS name option on the VPC endpoint. This page focuses on inbound PrivateLink DNS configuration.
Architecture overview
The following diagrams illustrate the two DNS resolution patterns for AWS PrivateLink. The pattern you choose depends on your organizational requirements for endpoint management and isolation.
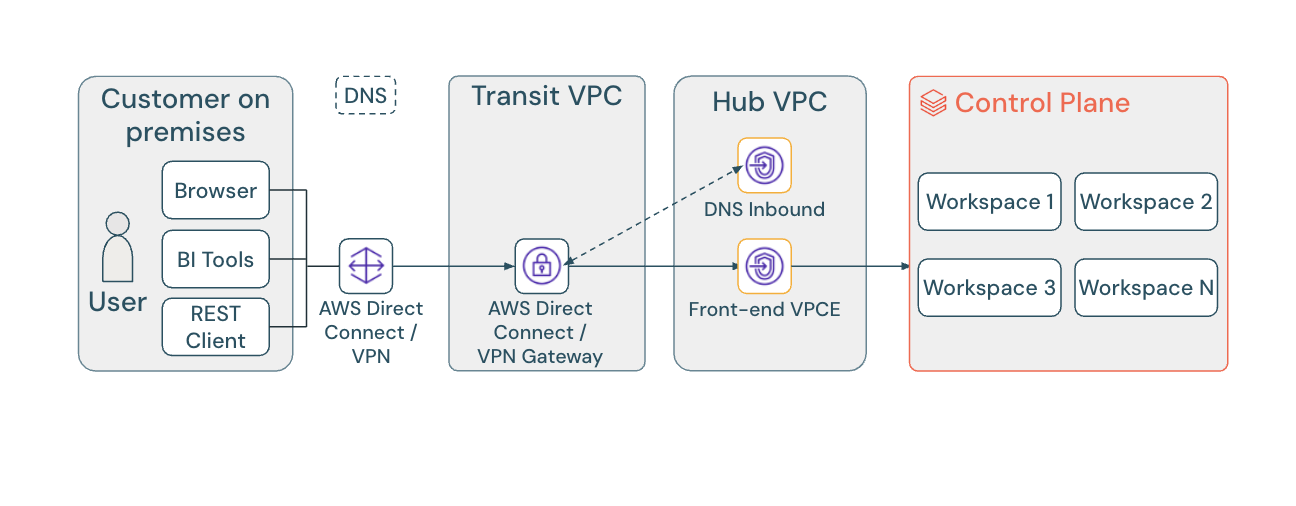
The single endpoint approach routes all workspaces in a region through one shared VPC endpoint, simplifying DNS configuration and management. This page defaults to this recommended approach for all configuration instructions.
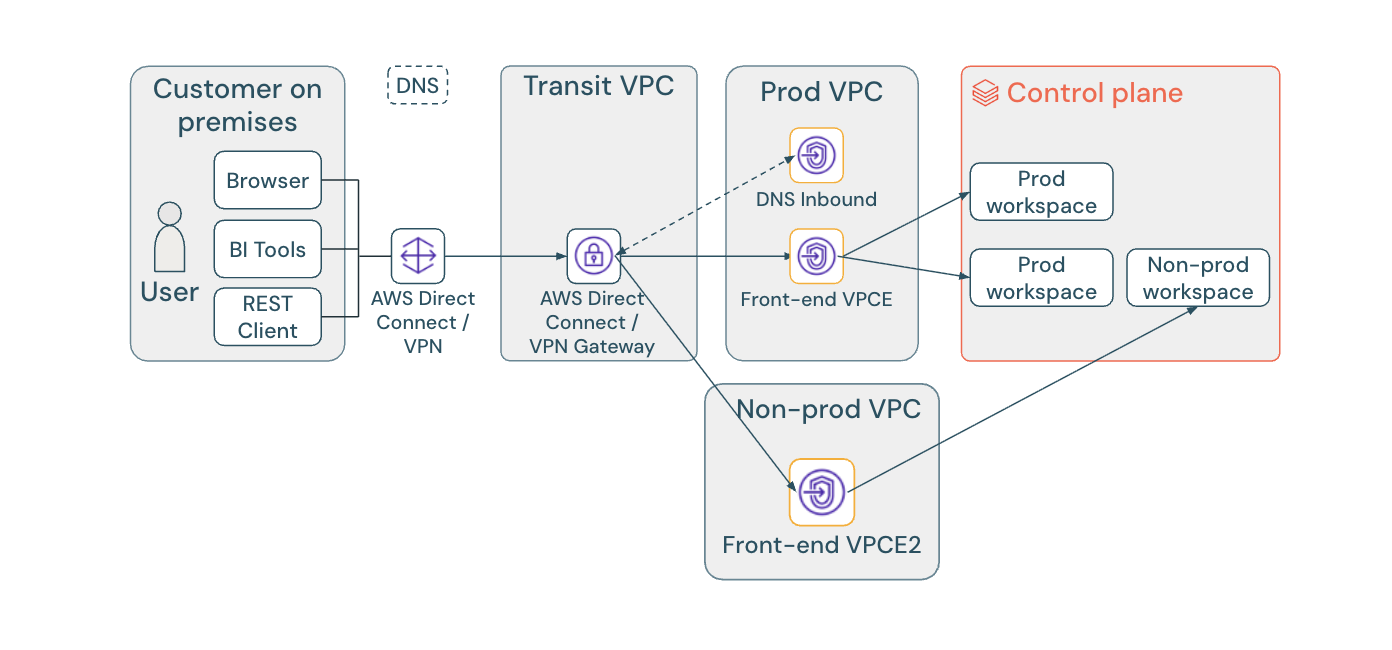
The multi-endpoint approach provides dedicated VPC endpoints for each workspace, enabling workspace-level network isolation at the cost of increased complexity.
DNS resolution with PrivateLink
Without PrivateLink, workspace URLs resolve to public IP addresses through a regional hostname like sydney.cloud.databricks.com, which points to a public AWS Elastic Load Balancer. For example:
$ nslookup myworkspace.cloud.databricks.com
myworkspace.cloud.databricks.com canonical name = sydney.cloud.databricks.com
sydney.cloud.databricks.com canonical name = public-ingress-xxxxx.elb.ap-southeast-2.amazonaws.com
Name: public-ingress-xxxxx.elb.ap-southeast-2.amazonaws.com
Address: 3.26.4.13
After you attach a private access settings object to a workspace, Databricks updates the DNS resolution chain to include the privatelink subdomain:
$ nslookup myworkspace.cloud.databricks.com
myworkspace.cloud.databricks.com canonical name = sydney.privatelink.cloud.databricks.com
Name: sydney.privatelink.cloud.databricks.com
Address: 10.176.10.182
The workspace URL now resolves to sydney.privatelink.cloud.databricks.com, which you configure to point to your VPC endpoint's private IP address. This allows you to override only the privatelink.cloud.databricks.com domain without affecting other Databricks services.
After you attach a private access settings object to a workspace, you cannot remove it. You can only replace it with a different private access settings object. This configuration is permanent.
DNS resolution
The specific DNS records you need depend on your configuration approach, but all configurations resolve workspace URLs to the private IP address of your inbound VPC endpoint.
- Single endpoint approach (recommended)
- Multi-endpoint approach
For most deployments, configure DNS to resolve the regional endpoint to your VPC endpoint's private IP. All workspaces in a region share the same VPC endpoint.
On-premises DNS configuration
Configure conditional forwarding in your corporate DNS to forward Databricks domain queries to AWS:
Domain | Forwarding target |
|---|---|
*.cloud.databricks.com | AWS DNS endpoint (Route 53 inbound resolver) |
*.aws.databricksapps.com | AWS DNS endpoint (Route 53 inbound resolver) |
Private Hosted Zone configuration
Create a Private Hosted Zone for the privatelink.cloud.databricks.com domain:
Configuration | Value |
|---|---|
Private Hosted Zone | privatelink.cloud.databricks.com |
Record name |
|
Record type | A (Alias) |
Record value | VPC endpoint ID |
The region value is the Databricks region name, for example, sydney, virginia, oregon, not the AWS region name. To find the correct region name for your workspace, see the Control plane services, including webapp row in Inbound IPs to Databricks control plane.
All workspaces in the same region that use inbound PrivateLink can share the same VPC endpoint and resolve to the same regional endpoint. This is the recommended approach for simplified management.
If you need separate VPC endpoints for individual workspaces, create workspace-specific Private Hosted Zones with ALIAS records. This approach provides network isolation between workspaces at the cost of increased complexity.
On-premises DNS configuration
Configure conditional forwarding in your corporate DNS to forward Databricks domain queries to AWS:
Domain | Forwarding target |
|---|---|
*.cloud.databricks.com | AWS DNS endpoint (Route 53 inbound resolver) |
*.aws.databricksapps.com | AWS DNS endpoint (Route 53 inbound resolver) |
Production VPC DNS configuration
Create a workspace-specific Private Hosted Zone in your production VPC:
Configuration | Value |
|---|---|
Private Hosted Zone |
|
Record type | A (Alias) |
Record value | VPC endpoint ID |
Replace <workspace> with your workspace deployment name (for example, myworkspace.cloud.databricks.com).
Non-production VPC DNS configuration
Create a workspace-specific Private Hosted Zone in your non-production VPC:
Configuration | Value |
|---|---|
Private Hosted Zone |
|
Record type | A (Alias) |
Record value | VPC endpoint ID |
Replace <workspace2> with your workspace deployment name (for example, myworkspace-dev.cloud.databricks.com).
Using per-workspace endpoints requires creating a DNS entry for each workspace and increases management complexity. Use this approach only when you need isolated VPC endpoints per workspace for specific security or networking requirements.
For a VPC in a separate AWS account:
- When you create the alias record, enter the full DNS of the VPC endpoint. For example,
vpce-xxx-xxx.vpce-svc-xxx.us-east-1.vpce.amazonaws.com. The endpoint won't appear in the available endpoints list. - Click Create.
AWS automatically resolves these names globally for cross-account DNS. You don't need AWS RAM for cross-account DNS.
Configuration options
- Conditional forwarding to Route 53 for single endpoint (recommended)
- Conditional forwarding to Route 53 for multi-endpoint
- Manual DNS zone and records
Configure your corporate DNS to forward queries for Databricks domains to Amazon Route 53. AWS automatically resolves workspace URLs to private IPs without manual record management. This approach uses a single VPC endpoint for all workspaces in a region.
Benefits of conditional forwarding
- Automatic resolution: Route 53 automatically resolves workspace URLs to private IPs when the VPC endpoint has the Enable DNS name option enabled.
- No manual updates: If VPC endpoint IPs change, Route 53 automatically updates DNS records.
- Simplifies management: A single configuration handles all workspaces in a region.
Prerequisites
Before you begin, verify that you have:
- A inbound PrivateLink VPC endpoint with Enable DNS name enabled
- Network connectivity between your corporate network and AWS using Direct Connect or VPN
- Permissions to create Route 53 resources and modify your corporate DNS
Step 1: Create a private hosted zone
Create a private hosted zone in Route 53 for Databricks workspace DNS records.
- Go to the Route 53 Hosted zones page in the AWS Management Console.
- Click Create hosted zone.
- For Domain name, enter
privatelink.cloud.databricks.com. - For Type, select Private hosted zone.
- In the VPCs to associate section, select the VPC where your inbound VPC endpoint is located. This is typically your transit VPC.
- Click Create hosted zone.
Step 2: Create a DNS A record
Create an A record that maps the regional endpoint to your VPC endpoint's private IP address.
-
In the Route 53 console, select the
privatelink.cloud.databricks.comhosted zone you created. -
Click Create record.
-
For Record name, enter your Databricks region name (for example,
sydney,virginia,oregon). -
For Record type, select A - Routes traffic to an IPv4 address.
-
For Value, enter the private IP address of your inbound VPC endpoint.
To find the private IP:
- Go to the VPC endpoints page.
- Select your inbound VPC endpoint.
- In the Subnets tab, note the IPv4 address.
-
Click Create records.
Step 3: Create a Route 53 inbound resolver endpoint
Create an inbound resolver endpoint so your corporate DNS can forward queries to Route 53.
- Go to the Route 53 Resolver page.
- In the left navigation, click Inbound endpoints.
- Click Create inbound endpoint.
- Provide a name for the endpoint, such as
databricks-privatelink-resolver. - Select your VPC.
- For Security group, select or create a security group that allows inbound TCP and UDP traffic on port 53 from your on-premises network.
- In the IP addresses section:
- Select at least two subnets in different Availability Zones for high availability.
- For each subnet, either let AWS automatically assign an IP address or choose a specific IP address within the subnet range.
- Click Create inbound endpoint.
- Note the IP addresses of the inbound resolver endpoint for use in the next step.
Step 4: Configure conditional forwarding in your corporate DNS
Configure your corporate DNS server to forward queries for Databricks domains to the Route 53 inbound resolver endpoint.
The exact steps depend on your DNS software, such as BIND, Windows DNS, or Infoblox. See your DNS server documentation for specific configuration steps.
Configure conditional forwarding for the following domains:
*.cloud.databricks.com- Required for workspace URL resolution*.aws.databricksapps.com- Required if you use Databricks Apps
Forward these domains to the IP addresses of your Route 53 inbound resolver endpoint.
Verification
After you complete the configuration, test DNS resolution from your corporate network:
$ nslookup myworkspace.cloud.databricks.com
myworkspace.cloud.databricks.com canonical name = sydney.privatelink.cloud.databricks.com
Name: sydney.privatelink.cloud.databricks.com
Address: 10.176.10.182
The workspace URL should resolve to the private IP address of your VPC endpoint. If you see a public IP address, verify your conditional forwarding rules and Route 53 configuration.
Configure your corporate DNS to forward queries for Databricks domains to AWS Route 53. This approach uses separate VPC endpoints for individual workspaces, providing workspace-level network isolation.
Benefits of conditional forwarding
- Automatic resolution: Route 53 automatically resolves workspace URLs to private IPs when the VPC endpoint has the Enable DNS name option enabled.
- No manual updates: If VPC endpoint IPs change, Route 53 automatically updates DNS records.
- Workspace isolation: Each workspace uses a dedicated VPC endpoint for network isolation.
Prerequisites
Before you begin, verify that you have:
- A inbound PrivateLink VPC endpoint with Enable DNS name enabled for each workspace
- Network connectivity between your corporate network and AWS using Direct Connect or VPN
- Permissions to create Route 53 resources and modify your corporate DNS
Step 1: Create a Private Hosted Zone
Create a workspace-specific Private Hosted Zone in Route 53 for each workspace.
- Go to the Route 53 Hosted zones page in the AWS Management Console.
- Click Create hosted zone.
- For Domain name, enter your workspace deployment name (for example,
myworkspace.cloud.databricks.comormyworkspace-dev.cloud.databricks.com). - For Type, select Private hosted zone.
- In the VPCs to associate section, select the VPC where your inbound VPC endpoint is located.
- Click Create hosted zone.
- Repeat this process for each workspace that requires a separate VPC endpoint.
Step 2: Create a DNS A record
Create an A alias record that maps the workspace URL to your VPC endpoint.
-
In the Route 53 console, select the workspace-specific hosted zone you created (for example,
myworkspace.cloud.databricks.com). -
Click Create record.
-
Leave Record name blank (the record applies to the zone apex).
-
For Record type, select A - Routes traffic to an IPv4 address.
-
Enable the Alias toggle and select Alias to VPC endpoint. Then select your workspace's VPC endpoint ID from the list.
For a VPC endpoint in a separate AWS account:
- Enter the full DNS name of the VPC endpoint (for example,
vpce-xxx-xxx.vpce-svc-xxx.us-east-1.vpce.amazonaws.com). The endpoint won't appear in the available endpoints list. - AWS automatically resolves these names globally for cross-account DNS. You don't need AWS Resource Access Manager for cross-account DNS.
- Enter the full DNS name of the VPC endpoint (for example,
-
Click Create records.
-
Repeat this process for each workspace.
Using per-workspace endpoints requires creating a DNS entry for each workspace and increases management complexity. Use this approach only when you need isolated VPC endpoints per workspace for specific security or networking requirements.
Step 3: Create a Route 53 inbound resolver endpoint
Create an inbound resolver endpoint so your corporate DNS can forward queries to Route 53.
- Go to the Route 53 Resolver page.
- In the left navigation, click Inbound endpoints.
- Click Create inbound endpoint.
- Provide a name for the endpoint, such as
databricks-privatelink-resolver. - Select your VPC.
- For Security group, select or create a security group that allows inbound TCP and UDP traffic on port 53 from your on-premises network.
- In the IP addresses section:
- Select at least two subnets in different Availability Zones for high availability.
- For each subnet, either let AWS automatically assign an IP address or choose a specific IP address within the subnet range.
- Click Create inbound endpoint.
- Note the IP addresses of the inbound resolver endpoint for use in the next step.
Step 4: Configure conditional forwarding in your corporate DNS
Configure your corporate DNS server to forward queries for Databricks domains to the Route 53 inbound resolver endpoint.
The exact steps depend on your DNS software, such as BIND, Windows DNS, or Infoblox. See your DNS server documentation for specific configuration steps.
Configure conditional forwarding for the following domains:
*.cloud.databricks.com- Required for workspace URL resolution*.aws.databricksapps.com- Required if you use Databricks Apps
Forward these domains to the IP addresses of your Route 53 inbound resolver endpoint.
Verification
After you complete the configuration, test DNS resolution from your corporate network:
$ nslookup myworkspace.cloud.databricks.com
myworkspace.cloud.databricks.com canonical name = sydney.privatelink.cloud.databricks.com
Name: sydney.privatelink.cloud.databricks.com
Address: 10.176.10.182
The workspace URL should resolve to the private IP address of your VPC endpoint. If you see a public IP address, verify your conditional forwarding rules and Route 53 configuration.
If conditional forwarding to Route 53 isn't available in your environment, you can manually create a DNS zone and records in your corporate DNS server. This approach requires manual updates if VPC endpoint IP addresses change.
Benefits of manual DNS zone
Use manual DNS configuration when:
- You can't configure conditional forwarding to AWS Route 53
- Your corporate DNS policies require all DNS records to be managed internally
- You need full control over DNS record management
With manual DNS configuration, update the A records whenever your VPC endpoint IP addresses change. This can lead to connectivity issues if records become outdated.
Step 1: Create a DNS zone
In your corporate DNS server, create a zone for privatelink.cloud.databricks.com.
Step 2: Add A records
Create an A record that maps the regional endpoint to your VPC endpoint's private IP:
Record name | Record type | Value |
|---|---|---|
| A | Private IP of your inbound VPC endpoint |
For example, if your workspace is in the Sydney region and your VPC endpoint has the IP address 10.176.10.182, create an A record for sydney.privatelink.cloud.databricks.com pointing to 10.176.10.182.
Verification
Test DNS resolution from your corporate network:
$ dig +short myworkspace.cloud.databricks.com
sydney.privatelink.cloud.databricks.com
10.176.10.182
The workspace URL should resolve to the private IP address of your VPC endpoint.
Special deployment scenarios
- Mixed deployments
- Hybrid access (private and public endpoints)
- Databricks Apps domains
You can have some workspaces using inbound PrivateLink and others using public endpoints in the same account. DNS resolution automatically handles this scenario.
Workspaces without a private access settings object resolve to public IP addresses using <region>.cloud.databricks.com. Workspaces with a private access settings object resolve to <region>.privatelink.cloud.databricks.com and use the private IP.
No additional DNS configuration is required for mixed deployments.
You can configure a workspace to be accessible from both private endpoints using PrivateLink and public endpoints using the internet.
To enable hybrid access:
- When creating a Private Access Settings object, set Public access enabled to True.
- The workspace is now accessible through both PrivateLink and public internet.
- Users on your corporate network with private DNS configured automatically use the private endpoint.
- Users outside your corporate network use the public endpoint.
To restrict which public IP addresses can access the workspace, configure IP access lists. This allows you to allowlist specific source IP addresses, such as those from trusted third-party SaaS applications.
Databricks Apps use the domain *.aws.databricksapps.com. These domains use a CNAME record that resolves to dbc-<workspace-deployment-id>.cloud.databricks.com, which resolves to the regional endpoint.
For example:
$ nslookup natural-language-to-qdrant-1016658646341465.aws.databricksapps.com
natural-language-to-qdrant-1016658646341465.aws.databricksapps.com
canonical name = dbc-35bfa1f1-1292.cloud.databricks.com
dbc-35bfa1f1-1292.cloud.databricks.com
canonical name = oregon.cloud.databricks.com
If you use conditional forwarding for *.cloud.databricks.com, apps domains automatically resolve correctly. If you use manual DNS configuration, you also need to forward *.aws.databricksapps.com or create corresponding records.
For more information about Databricks Apps networking, see Ingress controls.
Verification
After configuring DNS, verify that workspace URLs resolve correctly to private IP addresses.
- Use nslookup
- Use dig
- Test workspace access
From a machine on your corporate network, test workspace DNS resolution:
$ nslookup myworkspace.cloud.databricks.com
Expected output:
myworkspace.cloud.databricks.com canonical name = sydney.privatelink.cloud.databricks.com
Name: sydney.privatelink.cloud.databricks.com
Address: 10.176.10.182
The workspace URL should resolve through the privatelink subdomain to a private IP address, typically in the 10.x.x.x, 172.16.x.x, or 192.168.x.x range.
You can also use dig for more detailed DNS information:
$ dig +short myworkspace.cloud.databricks.com
sydney.privatelink.cloud.databricks.com
10.176.10.182
After verifying DNS resolution, test that you can access the workspace:
- From a machine on your corporate network or connected through VPN, open a web browser.
- Go to your workspace URL.
- Verify that you can log in and access the workspace.
If you can't access the workspace:
- Verify that your VPC endpoint has the Enable DNS name option enabled.
- Check that your Private Hosted Zone is associated with the correct VPC.
- Verify that your conditional forwarding rules are configured correctly in your corporate DNS.
- Confirm that network connectivity exists between your corporate network and the AWS VPC using Direct Connect or VPN.
- Check security group rules on your VPC endpoint allow inbound TCP traffic on port 443.
Common issues
DNS resolution returns public IPs: Your conditional forwarding rules aren't working correctly, or queries aren't reaching Route 53. Verify your DNS server configuration and Route 53 inbound resolver endpoint.
Workspace URL doesn't resolve: Your Private Hosted Zone may not have the correct A record, or the hosted zone isn't associated with the right VPC. Verify your Route 53 configuration.
Can't access workspace after DNS resolves: Check network connectivity and security group rules. Verify that your corporate network can reach the VPC endpoint's private IP on port 443.
What's next
- Enable inbound (front-end)PrivateLink: If you haven't already set up PrivateLink, see Configure Inbound PrivateLink.
- Enable classic compute plane (back-end) PrivateLink: Complete your private connectivity setup by configuring PrivateLink from your compute plane to the control plane. See Configure classic private connectivity to Databricks.
- IP access lists: Add an additional layer of security by controlling which public IP addresses can access your workspace. See Configure IP access lists for workspaces.