Manage context-based ingress policies
This feature is in Public Preview.
This page shows account admins how to create network policies, author granular ingress rules, and attach a policy to workspaces. For an overview of context-based ingress, see Context-based ingress control.
For serverless egress control, see What is serverless egress control?.
Requirements
- You must be an account admin.
- Your Databricks workspace must be on the Enterprise tier.
Enable context-based ingress
As an account admin, enable the context-based ingress preview in your account.
- As an account admin, log in to the account console.
- Click Previews.
- Set the Context-based Ingress Control toggle to On.
Access network policies
Use a network policy to define ingress and egress rules for one or more workspaces. To create, view, and update network policies in your account:
- From the account console, click Security.
- Click the Networking tab.
- Under Policies, click Context-based ingress & egress control.
The default policy applies to any workspace without another network policy. Databricks doesn't recommend modifying its ingress rules. Instead, create a new policy and attach it to specific workspaces.
Create a network policy
- Click Create new network policy.
- Enter a Policy name.
- Click the Ingress tab. To set egress rules, see Set egress rules.
- Select a network access mode:
- Allow access from all sources: Allow unrestricted inbound access over the internet.
- Restrict access based on request context: Deny inbound internet access by default and allow access only through explicit Allow rules. For details, see Context-based ingress control.
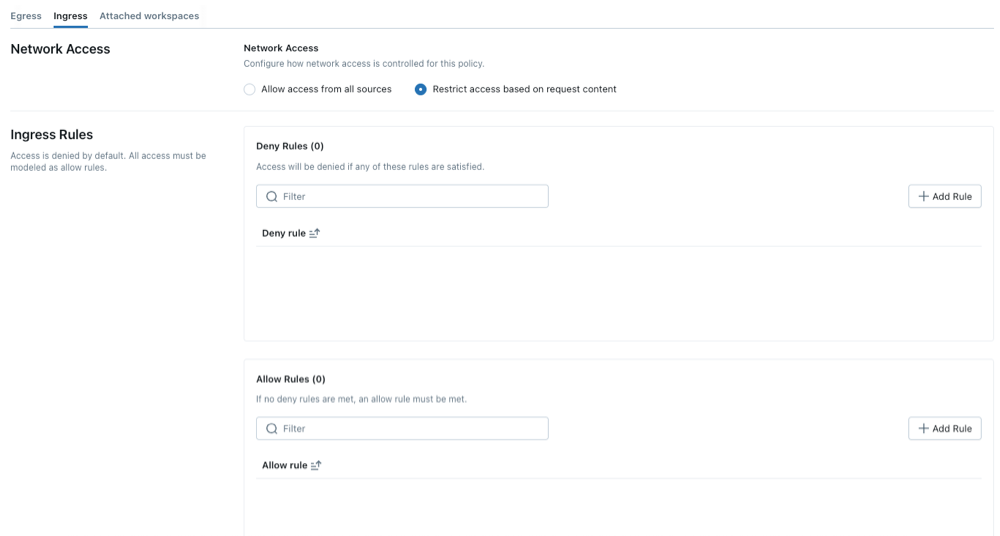
Configure network policies
When you use restricted access mode:
- The policy denies access by default.
- The policy grants access only when a request matches an explicit Allow rule.
- Deny rules are exceptions to Allow rules. For example, you can allow a broad network range while denying access to specific identities within that range. If a request matches both an allow rule and a deny rule, the request is denied.
The following steps outline optional settings for restricted access mode.
Set ingress rules
-
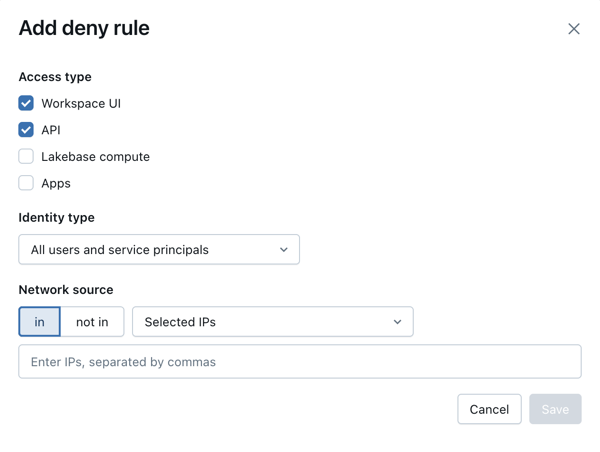
To configure allow or deny rules, click Add rule above the Allow rules or Deny rules lists.
-
Select an access type:
- Workspace UI: Allow access to the workspace UI.
- API: Allow or deny access to Databricks APIs.
- Lakebase Compute: Allow access to Lakebase database instances. See Create and manage a database instance.
- Apps: Allow access to Databricks Apps deployments.
-
Select an identity type:
- All users and service principals: Allow access to both users and service principals.
- All users: Allow access only to users in the workspace.
- All service principals: Allow access only to service principals in the workspace.
- Selected identities: Allow access only to specific users or service principals. Choose the identities from the Subjects list.
noteFor Lakebase Compute and Apps access types, the only supported identity type is All users and service principals. Other identity options cannot be selected.
-
Select a network source:
- All public IPs: Allow access from all public IPs.
- Selected IPs: Allow access from only specific IPs. Enter the IPs separated by commas.
For Deny rules with selected IPs, choose one of the following:
- IN: Denies access from IPs that are in the specified network source.
- NOT IN: Denies access from IPs that are not in the specified network source.
-
Click Save.
You can define multiple allow and deny rules to control access based on client identity, client network source, or access scope (access type).
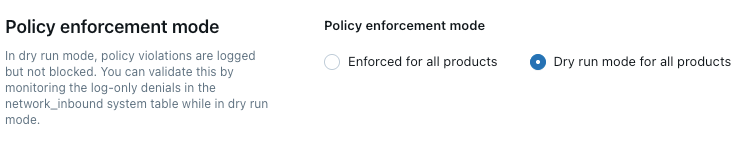
Set a policy enforcement mode
Dry-run mode allows you to test your policy configuration and monitor inbound connections without disrupting access to resources. When dry-run mode is enabled, requests that violate the policy are logged but not blocked.
- Set the policy enforcement mode to Enforced for all products or Dry run mode for all products.
- Click Create.
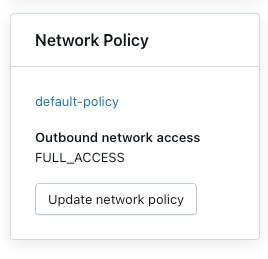
Attach a network policy to workspaces
If you have updated your default policy with additional configurations, they are automatically applied to workspaces that don't have an existing network policy.
To associate your workspace with a different policy, follow these steps:
- In the account console, click Workspaces.
- Select a workspace.
- In Network Policy, click Update network policy.
- Select the desired network policy from the list.
- Click Apply policy.
Check denial logs
Denial logs are stored in the system.access.inbound_network table in Unity Catalog. These logs track when inbound network requests are denied. To access denial logs, verify the access schema is enabled on your Unity Catalog metastore. See Enable system tables.
Use a SQL query like the following example to view denial events. If dry-run logs are enabled, the query returns both denial logs and dry-run logs, which you can distinguish using the access_type column. Denial logs have a DROP value, while dry-run logs show DRY_RUN_DENIAL.
The following example retrieves logs from the last 2 hours:
SELECT *
FROM system.access.inbound_network
WHERE event_time >= CURRENT_TIMESTAMP() - INTERVAL 2 HOUR
ORDER BY event_time DESC;
Logs might not appear immediately. There might be a delay of several minutes between the time of access and when the denial logs appear.