Use an identity provider token to authenticate to Databricks
In this article, you will follow the steps for passing a token from a federated identity provider to securely call Databricks REST APIs and access your Databricks resources.
Databricks OAuth federation is in Public Preview.
Before you begin
Before you start this task, you must have configured a federation policy for your Databricks account or service principal.
After you have configured it, you can obtain and use a JSON web token (JWT) from your identity provider to access Databricks APIs. Tokens must be valid JWTs that are signed using the RS256 or ES256 algorithms.
The process for authenticating access to Databricks APIs starting with a token from a federated identity provider is:
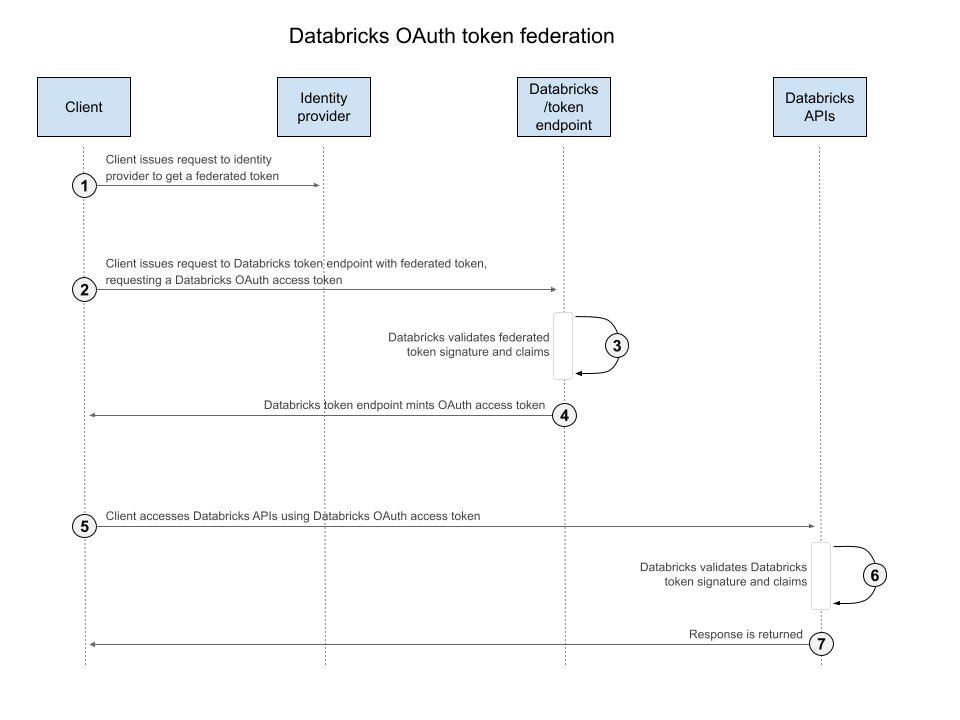
- Issue a request to an identity provider to get a federated JWT. The details of how to get a federated JWT will vary depending on the identity provider. Consult your identity provider documentation or an administrator for details.
- Exchange the JWT from your identity provider for a Databricks OAuth token.
- Use the Databricks OAuth token to access Databricks APIs.
Step 1: Issue a request to an identity provider to get a federated JWT
The details of how to get a federated JWT will vary depending on the identity provider. Consult your identity provider documentation or an administrator for details.
Step 2: Exchange a JWT from your identity provider for a Databricks OAuth token
You exchange a JWT from your identity provider for a Databricks OAuth token by sending a request to the Databricks token endpoint for your account or workspace, using the OAuth 2.0 Token Exchange (RFC 8693).
For example, this command exchanges a federated JWT from your identity provider for a Databricks OAuth token using an account federation policy:
curl --request POST https://<databricks-workspace-host>/oidc/v1/token \
--data "subject_token=${FEDERATED_JWT_TOKEN}" \
--data 'subject_token_type=urn:ietf:params:oauth:token-type:jwt' \
--data 'grant_type=urn:ietf:params:oauth:grant-type:token-exchange' \
--data 'scope=all-apis'
To use OAuth to access Databricks account resources, use the URL https://<databricks-account-host>/oidc/accounts/<account-id>/v1/token.
The following example command exchanges a federated JWT for a Databricks OAuth token using a service principal federation policy:
curl --request POST https://<databricks-workspace-host>/oidc/v1/token \
--data "client_id=${CLIENT_ID}" \
--data "subject_token=${FEDERATED_JWT_TOKEN}" \
--data 'subject_token_type=urn:ietf:params:oauth:token-type:jwt' \
--data 'grant_type=urn:ietf:params:oauth:grant-type:token-exchange' \
--data 'scope=all-apis'
Replace CLIENT_ID with the service principal UUID (for example, 11112222-bbbb-3333-cccc-4444dddd5555).
If the token from your identity provider is valid and matches your federation policy, you receive a standard JSON response that includes a Databricks OAuth token in the access_token field. This OAuth token can be used to access Databricks APIs. The resulting Databricks OAuth token has the same expiration (exp) claim as the JWT provided in the subject_token parameter.
The following is an example OAuth token endpoint response:
{
"access_token": "eyJraWQ...odi0WFNqQw",
"scope": "all-apis",
"token_type": "Bearer",
"expires_in": 3600
}
Step 3: Use the exchanged Databricks OAuth token to authenticate to the Databricks API
You can then use the resulting Databricks OAuth token as a bearer token to access Databricks APIs. For example, to call the Databricks SCIM Me API to retrieve your Databricks user and display name:
TOKEN='<your-databricks-oauth-token>'
curl --header "Authorization: Bearer $TOKEN" \
--url https://${DATABRICKS_WORKSPACE_HOSTNAME}/api/2.0/preview/scim/v2/Me
The response should appear similar to the following:
{
"userName": "username@mycompany.com",
"displayName": "Firstname Lastname"
}