Configure IP access lists for the account console
This page describes how to configure IP access lists for the Databricks account console. You can also use the Account IP Access Lists API. To configure IP access lists for a Databricks workspace, see Configure IP access lists for workspaces.
Requirements
- This feature requires the Enterprise pricing tier.
- IP access lists support only Internet Protocol version 4 (IPv4) addresses.
If you have serverless jobs, notebooks, or other serverless compute resources that interact with the Databricks account console, and you have enabled account-level IP access lists, additional IP addresses not listed on this page might be required in your allowlist. We recommend that you reach out to your Databricks account team for support.
Enable IP access lists
Account admins can enable and disable IP access lists for account console. When IP access lists is enabled, users can only access the account console through IPs on the allow list. When IP access lists is disabled, all existing allow lists or block lists are ignored and all IP addresses can access the account console. By default, new IP access lists for the account console take effect within a few minutes.
- In the sidebar, click Security.
- Under Policies, select Account console IP access list.
- Set the Enabled/disabled toggle to Enabled.
Add an IP access list
-
In the sidebar, click Security.
-
Under Policies, select Account console IP access list.
-
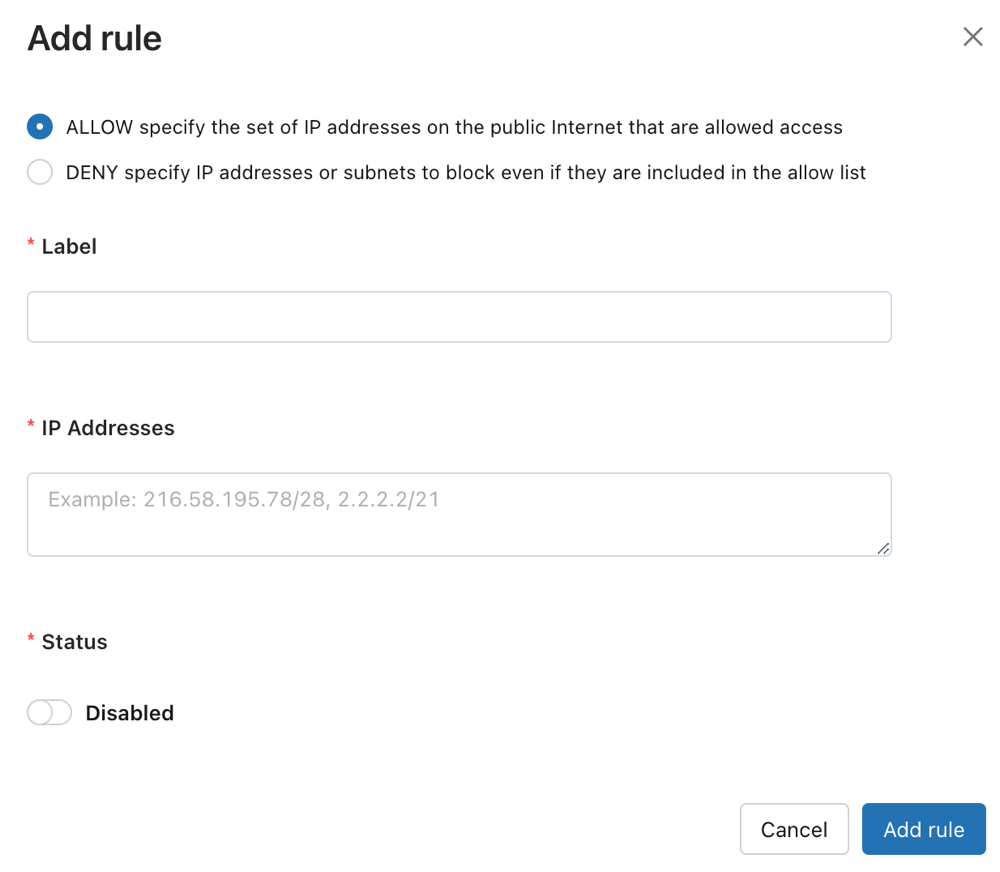
Click Add rule.
-
Choose whether to make an ALLOW or BLOCK list.
-
In the label field, add a human-readable label.
-
Add one or more IP addresses or CIDR IP ranges, with commas separating them.
-
Click Add rule.
Delete an IP access list
- In the sidebar, click Security.
- Under Policies, select Account console IP access list.
- On the row for the rule, click the kebab menu
on the right, and select Delete.
- Confirm deletion in the confirmation popup that appears.
Disable an IP access list
- In the sidebar, click Security.
- Under Policies, select Account console IP access list.
- In the Status column, click the Enabled button to toggle between enabled and disabled.
Update an IP access list
- In the sidebar, click Security.
- Under Policies, select Account console IP access list.
- On the row for the rule, click the kebab menu
on the right, and select Update.
- Update any fields.
- Click Update rule.
Next steps
- Configure IP access lists for workspaces: Implement IP restrictions for workspace access to control which networks can connect to your Databricks workspaces. See Configure IP access lists for workspaces.
- Configure private connectivity: Use PrivateLink to establish secure and isolated access to AWS services from your virtual network, bypassing the public internet. See Configure classic private connectivity to Databricks.
- Set up customer-managed VPC: Configure your own VPC with proper NAT gateway settings to ensure IP access list compatibility. See Configure a customer-managed VPC.