Configure SSO para seu workspace (legado)
workspace-level SSO é uma configuração herdada. Ele só pode ser configurado quando o login unificado está desativado. Quando o login unificado está ativado, o workspace usa a mesma configuração do SSO que o account.
Se o seu account foi criado após 21 de junho de 2023 ou se o senhor não configurou o SSO antes de 12 de dezembro de 2024, o login unificado está ativado no seu account para todos os espaços de trabalho, novos e existentes, e não pode ser desativado.
Databricks recomenda ativar o login unificado em todos os espaços de trabalho. Consulte Habilitar login unificado.
Essa documentação foi descontinuada e pode não estar atualizada.
Este artigo mostra como configurar o logon único (SSO) para autenticar o espaço de trabalho Databricks usando o provedor de identidade da sua organização. Para sincronizar usuários e grupos do seu provedor de identidade, consulte Sincronizar usuários e grupos do seu provedor de identidade usando o SCIM.
Visão geral da configuração do site workspace SSO
O single sign-on no nível do espaço de trabalho (SSO) permite que o senhor autentique os usuários no seu Databricks workspace usando o provedor de identidade da sua organização. SSO para usuários do workspace requer o protocolo SAML 2.0.
que não estejam na versão E2 da plataforma Databricks default para a versão 1 de SAML. Para atualizar um workspace para usar a versão 2, entre em contato com a equipe do Databricks account .
workspace-level SSO só pode ser configurado quando o login unificado estiver desativado. Quando o workspace-level SSO está ativado, todos os usuários, inclusive os administradores, devem fazer login no workspace usando o logon único.
Login unificado
O login unificado permite que o senhor gerencie uma configuração SSO para seu Databricks account e espaço de trabalho. Quando o SSO está ativado no seu account, o senhor pode optar por ativar o login unificado para todo o espaço de trabalho ou para o espaço de trabalho selecionado. O espaço de trabalho de login unificado usa a configuração account-level SSO e todos os usuários, incluindo os administradores account e workspace, devem fazer login em Databricks usando SSO. O senhor não pode gerenciar SSO separadamente no nível workspace em um workspace habilitado para login unificado. Databricks recomenda que o senhor ative o login unificado para todos os espaços de trabalho.
Se o seu account foi criado após 21 de junho de 2023 ou se o senhor não configurou o SSO antes de 12 de dezembro de 2024, o login unificado está ativado no seu account para todos os espaços de trabalho, novos e existentes, e não pode ser desativado.
Para ativar o login unificado, consulte Habilitar login unificado.
workspace SSO exemplos de aplicação
Você pode ler as instruções sobre como configurar o SSO para os seguintes provedores de identidade:
- Configure SSO para seu workspace (legado)
- Configure AWS IAM Identidade SSO para o seu workspace
- SSO com Microsoft Entra ID para o senhor workspace
- SSO com Google Workspace (GSuite) para seu workspace
- Configurar SSO com Okta para seu workspace
- Configurar SSO com OneLogin para seu workspace
- Configurar SSO com Ping Identity para seu workspace
O processo é semelhante para qualquer provedor de identidade compatível com SAML 2.0. Se o seu provedor de identidade não estiver listado acima, siga as instruções abaixo.
Ativar workspace-level single sign-on
workspace-level SSO só pode ser configurado quando o login unificado estiver desativado. Consulte Login unificado.
Para evitar ser bloqueado no Databricks durante os testes de login único, o Databricks sugere manter o console da conta aberto em uma janela de navegador separada.
-
Acesse as workspace configurações de administrador do site e selecione Identidade e tab acesso.
-
Clique em gerenciar ao lado de SSO settings .
-
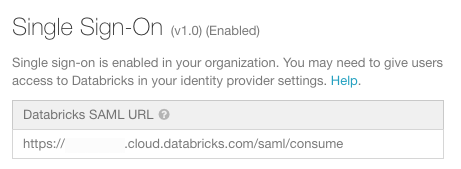
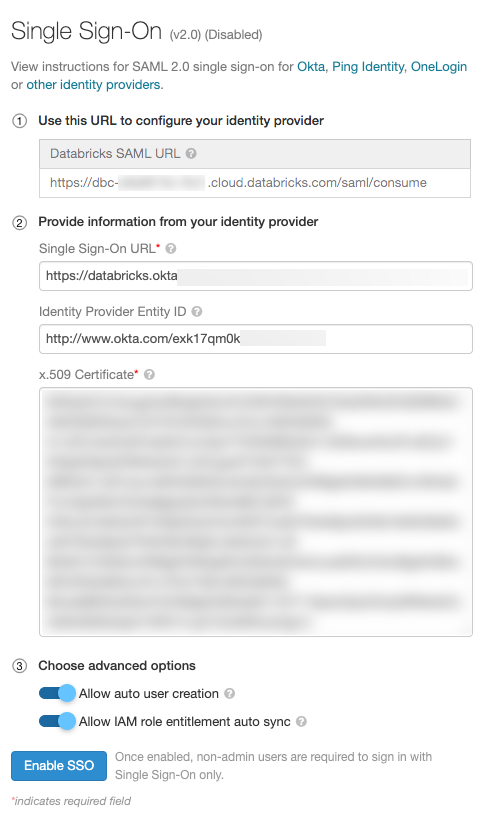
Acesse seu provedor de identidade e crie um aplicativo Databricks com as informações no campo Databricks SAML URL .
-
No campo Fornecer as informações do provedor de identidade, cole as informações de seu provedor de identidade no endereço Databricks SSO.
-
(Opcional) Ative a criação automática de usuários, selecione Permitir criação automática de usuários . A criação automática de usuários permite que os usuários no provedor de identidade acessem log in no site workspace. Se o endereço account do usuário ainda não existir em Databricks, um novo account será provisionado para ele no momento do login. Isso também é conhecido como provisionamento just-in-time (JIT). A criação automática de usuários não associa usuários a grupos.
-
Se estiver configurando a passagem de credenciais do IAM com a federação SAML 2.0, selecione Allow IAM role entitlement auto sync (Permitir sincronização automática de direitos de função do IAM ).
-
Clique em Ativar SSO .
Migrar os usuários existentes para o SSO
Quando a criação automática de usuário estiver ativada e o endereço email (nome de usuário) atual de um usuário com Databricks for o mesmo do provedor de identidade, a migração será automática e o senhor poderá ignorar esta etapa.
Se o endereço email de um usuário no provedor de identidade for diferente do endereço Databricks, um novo usuário baseado no provedor de identidade email aparecerá em Databricks quando ele fizer login. Como os usuários não administradores não poderão mais acessar log in usando o endereço email e a senha antigos, eles não poderão acessar os arquivos na pasta Users existente.
Recomendamos as seguintes passos para migrar arquivos de sua antiga pasta de usuários para sua nova pasta de usuários:
-
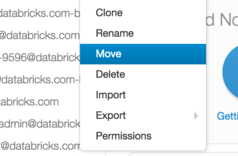
Um administrador do workspace pode remover o usuário antigo. Isso marca o diretório de pastas do usuário como extinto e o diretório seguirá todos os usuários ativos na lista de pastas workspace. Todos os Notebooks e bibliotecas ainda poderão ser acessados pelos administradores do site workspace. Todos os clusters e trabalhos criados pelo usuário permanecerão como estão. Se o usuário tiver outras ACLs definidas, a ativação do SSO fará com que elas sejam redefinidas, e o administrador do workspace deverá definir manualmente essas ACLs para o novo usuário.
-
O administrador do workspace pode então mover a pasta do usuário antigo para a nova pasta, conforme mostrado na figura a seguir.
Solução de problemas
A Databricks recomenda a instalação da extensão SAML Tracer para Chrome ou Firefox. O SAML Tracer permite que o senhor examine a solicitação SAML enviada do Databricks para o IdP e a resposta SAML enviada do IdP para o Databricks.
Se não conseguir resolver o problema usando as dicas de solução de problemas a seguir, entre em contato com a equipe de suporte da Databricks.
Verificar a versão e o URL do SSO
- Vá para as configurações de administrador e clique em Identity and access (Identidade e acesso ) tab.
- Clique em gerenciar ao lado de SSO settings .
- Verifique a versão do SSO, que está entre parênteses ao lado de Authentication (Autenticação ).
- Verifique o URL SAML da Databricks. Você fornece esse URL para o IdP. Esse URL será alterado se o senhor atualizar o site workspace para a versão E2 da plataforma Databricks ou se o site workspace for atualizado para a versão 2 do SSO.
Verificar se a resposta SAML está assinada
Se a resposta SAML não for assinada, o login poderá falhar com um erro como We encountered an error logging you in. Databricks support has been alerted and will begin looking into this issue right away.
Siga estas etapas com o SAML Tracer instalado em seu navegador.
- Em uma janela anônima, abra o SAML Tracer acessando Tools (Ferramentas) > SAML Tracer .
- Acesse o site Databricks workspace e tente acessar log in usando SSO.
- Em SAML Tracer, acesse a resposta tab.
- Se a resposta for assinada, o elemento
<saml2p:Response>terá um elemento filho<ds:signature>. Se a resposta não for assinada, configure seu IdP para assinar a resposta SAML. Para obter detalhes sobre como configurar seu IdP, siga o link para seu IdP no espaço de trabalho SSO application examples.
- Se a resposta for assinada, o elemento