Configure authorization in a Databricks app
Databricks Apps supports secure application development on Databricks. As apps access data and services within a workspace, they must use authentication and authorization mechanisms that enforce data access controls and respect user permissions. The Databricks Apps authorization model is based on OAuth 2.0 and combines the permissions assigned to the app with those of the user accessing it.
To support this framework, Databricks Apps uses two complementary identity models:
- App authorization gives the app its own identity with a consistent set of permissions.
- User authorization allows the app to use the identity and permissions of the user interacting with it.
App authorization
Each Databricks app has a dedicated service principal that acts as its identity when it accesses Databricks resources. This service principal is unique to the app instance and can't be reused across apps. You can't change the service principal assigned to an app or specify an existing service principal during app creation. Databricks uses this identity to evaluate the app's permissions independently of any user, which ensures that the app can only access resources explicitly granted to it, even outside the context of user interaction.
This separation helps enforce security boundaries, which enables auditing of app activity and supports scenarios like background processing or automated tasks.
The service principal is represented by a unique ID. Copy it from the app’s Authorization tab:
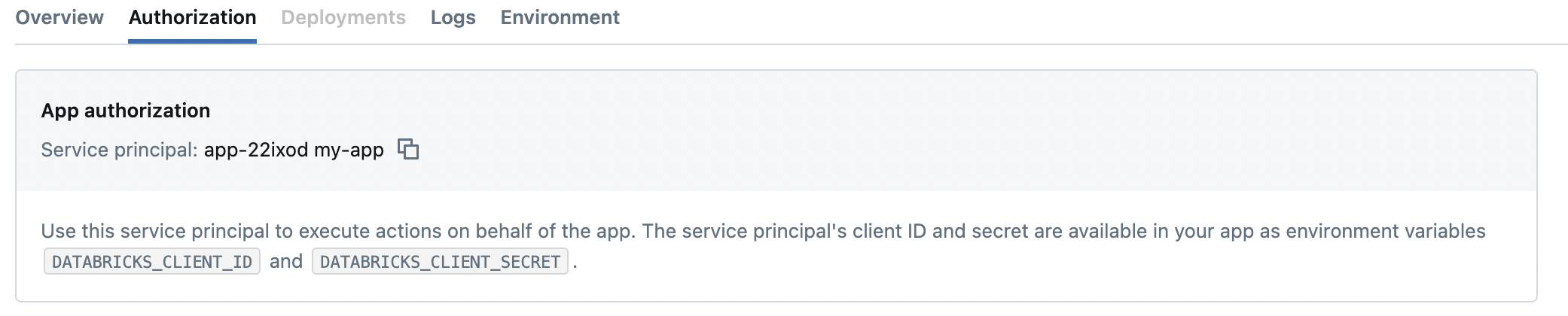
When you create an app, Databricks automatically provisions a dedicated service principal for the app. The service principal remains the same across all deployments of the app. When you delete the app, Databricks deletes the service principal.
Use the service principal for actions that the app performs on its own, without requiring the context of an individual user. Common use cases include:
- Running background tasks
- Reading or writing shared configuration or metadata
- Logging activity or usage metrics
- Calling external services through secure endpoints
All actions initiated by the app use the service principal’s permissions. Grant the service principal access to specific resources using standard permission assignments. However, it doesn’t support user-level access control. All users who interact with the app share the same permissions defined for the service principal, which prevents the app from enforcing fine-grained policies based on individual user identity.
The following example shows how an app uses its service principal to query data in Unity Catalog:
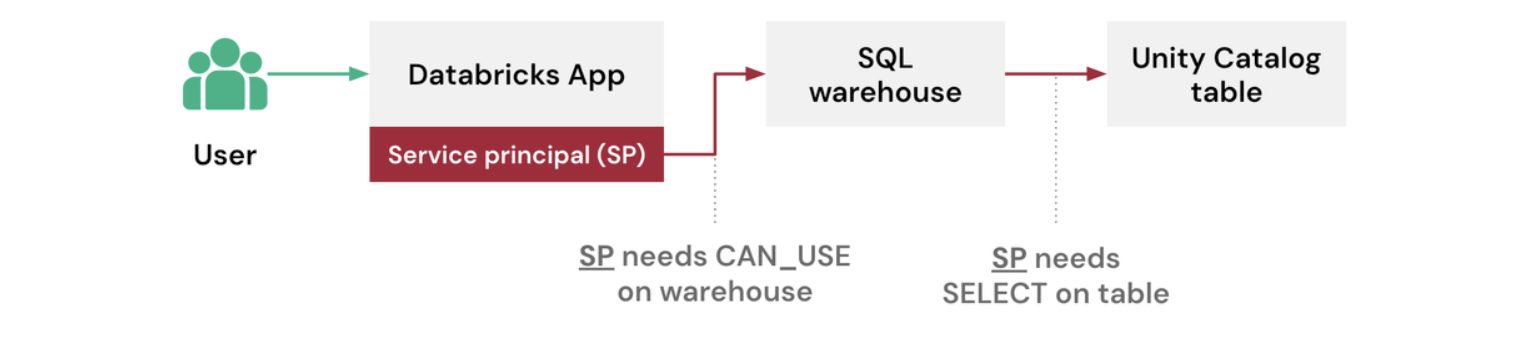
In this case, the service principal needs explicit access to both the SQL warehouse and the Unity Catalog table it queries.
This model works well when you want all users of the app to see the same data or when the app performs shared operations not tied to user-specific access controls.
Retrieve app authorization credentials
For app authorization, Databricks automatically injects service principal credentials into the app’s environment. The following environment variables hold the required OAuth client values:
Variable | Description |
|---|---|
| Service principal OAuth client ID |
| Service principal OAuth client secret |
Databricks sets the environment variables automatically in the app runtime. The app uses these variables when it authenticates as itself.
- Python
- JavaScript
import os
client_id = os.getenv('DATABRICKS_CLIENT_ID')
client_secret = os.getenv('DATABRICKS_CLIENT_SECRET')
const clientId = process.env.DATABRICKS_CLIENT_ID;
const clientSecret = process.env.DATABRICKS_CLIENT_SECRET;
If you're using the Databricks SDKs, you typically don’t need to manually access these environment variables. The SDKs follow unified authentication and automatically detect credentials in the environment.
Example: Query with app authorization
- Python
- JavaScript
This example uses the SDK Config object, which pulls service principal credentials from environment variables and performs OAuth authorization.
from databricks import sql
from databricks.sdk.core import Config
cfg = Config()
conn = sql.connect(
server_hostname=cfg.host,
http_path="<your-warehouse-http-path>",
credentials_provider=lambda: cfg.authenticate,
)
query = "SELECT * FROM main.sandbox.sales_customers LIMIT 1000"
with conn.cursor() as cursor:
cursor.execute(query)
df = cursor.fetchall_arrow().to_pandas()
print(df.head())
conn.close()
This example uses environment variables to authenticate with a service principal using OAuth and run a query with the Databricks SQL Driver for Node.js.
import { DBSQLClient } from '@databricks/sql';
const client = new DBSQLClient();
const connection = await client.connect({
authType: 'databricks-oauth',
host: process.env.DATABRICKS_SERVER_HOSTNAME,
path: process.env.DATABRICKS_HTTP_PATH,
oauthClientId: process.env.DATABRICKS_CLIENT_ID,
oauthClientSecret: process.env.DATABRICKS_CLIENT_SECRET,
});
const query = 'SELECT * FROM main.sandbox.sales_customers LIMIT 1000';
const cursor = await connection.cursor(query);
const rows = [];
for await (const row of cursor) {
rows.push(row);
}
console.log(rows.slice(0, 5)); // Like df.head()
await connection.close();
User authorization
User authorization is in Public Preview.
User authorization, sometimes referred to as on-behalf-of-user authorization, allows a Databricks Apps app to act with the identity of the app user. Databricks forwards the user’s access token to the app, which uses the token to access resources on the user's behalf. Databricks enforces all permissions based on the user’s existing Unity Catalog policies.
To manage the security risks of apps acting on a user's behalf, Databricks uses scopes to limit what actions an app can perform through user authorization.
Apply user authorization when the app needs to respect individual user permissions. Typical use cases include:
- Querying tables or volumes
- Accessing SQL warehouses or compute
- Running jobs or workflows tied to user actions
All actions use the existing Unity Catalog permissions of the user:
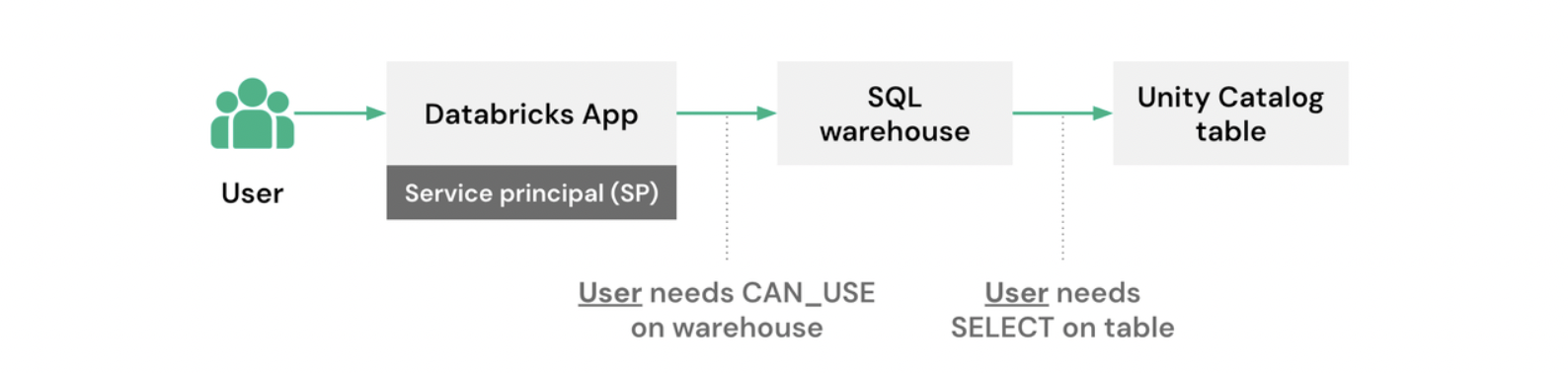
User authorization enables fine-grained access control by applying Unity Catalog features like row-level filters and column masks to app activity. This approach keeps access control consistent with workspace governance and avoids hardcoding permission logic into the app.
Fine-grained permissions with user authorization
When you add user authorization to an app, it enforces the user's existing Unity Catalog permissions, including:
- Row-level filters to restrict visible rows
- Column masks to redact or transform sensitive data
Because Databricks evaluates user authorization requests with the user’s identity, these policies apply automatically when the app accesses data. For example, if a table includes a row filter that limits visibility by region, the app only returns the rows that the user is allowed to query. No additional filtering logic is needed in the app.
This approach avoids duplicating access control logic in application code and ensures consistency with workspace-level governance. When admins update Unity Catalog policies, the app automatically respects those changes.
Scope-based security and privilege escalation
Apps that use user authorization must declare specific authorization scopes to limit what the app can do on the user's behalf. Scopes restrict access to specific APIs or resource types, such as:
sqlfor querying SQL warehousesdashboards.geniefor managing your Genie spacefiles.filesfor managing your files and directories
If you don't select any scopes, Databricks assigns a default set that allows the app to retrieve basic user identity information:
iam.access-control:readiam.current-user:read
These defaults are required to support user authorization functionality, but they don’t permit access to data or compute resources. Add additional scopes when you create or edit the app.
Scopes enforce the principle of least privilege. Make sure to configure the app to request only the scopes that it needs. Databricks blocks access to any functionality outside the approved scopes, even if the user has permission. For example, if the app requests only the sql scope, it can't access model serving endpoints, even if the user could outside the app.
When a user first accesses an app, Databricks prompts them to explicitly authorize the app to act within the requested scopes. After granting consent, users can't revoke it. Admins can optionally grant consent on behalf of users to align access with organizational policies.
Add scopes to an app
User authorization is in Public Preview. Your workspace admin must enable it before you can add scopes to your app.
After enabling user authorization, you must restart existing apps before you can add scopes to them. If you disable user authorization, you must restart existing apps in order for them to stop using the current user's access token to access resources.
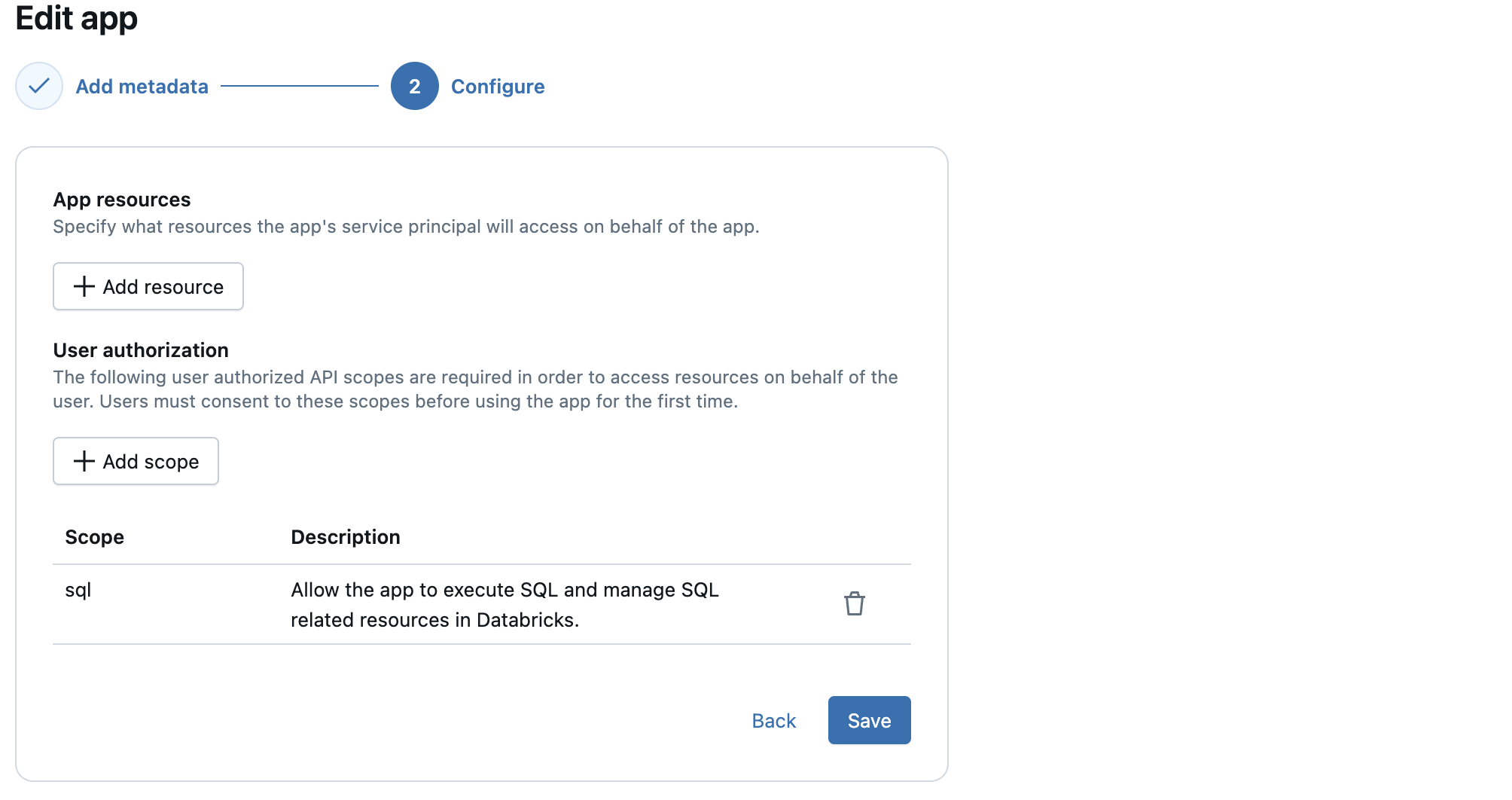
Configure user authorization when you create or edit an app in the Databricks UI.
In the Configure step, click +Add scope and select the scopes that define which Databricks APIs or resources the app can access on behalf of the user. Databricks enforces these scopes at runtime and requires user or admin consent before granting access.
For a complete example, see the Databricks Apps authorization demo on GitHub. The example app shows how to use both app and user authorization models, and includes setup instructions and example queries with user authorization.
Retrieve user authorization credentials
For user authorization, Databricks forwards the user’s identity and access token to the app in HTTP headers. The app must extract these headers to act on the user’s behalf.
How you retrieve these headers depends on the framework you use.
- Streamlit
- Gradio
- Dash and Flask
- Shiny
- Express
import streamlit as st
user_access_token = st.context.headers.get('x-forwarded-access-token')
import gradio as gr
def query_fn(message, history, request: gr.Request):
access_token = request.headers.get("x-forwarded-access-token")
...
Gradio automatically injects the request object into your app’s function if you declare it as a parameter. You don't have to construct or fetch the request manually.
from flask import request
headers = request.headers
user_token = headers.get('x-forwarded-access-token')
user_token = session.http_conn.headers.get('x-forwarded-access-token')
import express from 'express';
const userAccessToken = req.header('x-forwarded-access-token');
Example: Query with user authorization
In this case, the app passes the user’s access token directly to the connector, and Databricks applies the user’s permissions to the query.
- Python
- JavaScript
from databricks import sql
from databricks.sdk.core import Config
from flask import request
cfg = Config()
user_token = request.headers.get("x-forwarded-access-token")
conn = sql.connect(
server_hostname=cfg.host,
http_path="<your-warehouse-http-path>",
access_token=user_token
)
query = "SELECT * FROM main.sandbox.sales_customers LIMIT 1000"
with conn.cursor() as cursor:
cursor.execute(query)
df = cursor.fetchall_arrow().to_pandas()
print(df.head())
conn.close()
import { DBSQLClient } from '@databricks/sql';
import express from 'express';
const app = express();
app.get('/', async (req, res) => {
const userToken = req.header('x-forwarded-access-token');
const client = new DBSQLClient();
const connection = await client.connect({
authType: 'access-token',
host: process.env.DATABRICKS_SERVER_HOSTNAME,
path: process.env.DATABRICKS_HTTP_PATH,
token: userToken,
});
const query = 'SELECT * FROM main.sandbox.sales_customers LIMIT 1000';
const cursor = await connection.cursor(query);
const rows = [];
for await (const row of cursor) {
rows.push(row);
}
console.log(rows.slice(0, 5));
await connection.close();
res.send('Query complete');
});
app.listen(3000);
Best practices for user authorization
When you build apps that perform actions on behalf of users, follow these best practices to ensure secure and auditable access:
- Store app code in folders accessible only to the app owner or a small set of trusted users.
- Grant
CAN MANAGEpermissions only to trusted senior developers who are responsible for app maintenance and review. GrantCAN USEpermissions only to specific users or groups who are approved to run the app. - Ensure that tokens are not printed, logged, or written to files. This applies to all logging statements, debugging tools, and error handlers. For example, instead of
print(f"User token: {token}")useheaders = {"Authorization": f"Bearer {token}"}. - Configure each app to request only the minimum required authorization scopes needed for its functionality.
- During code review, verify that scope and permission settings align with security requirements and don't grant unnecessary access.
- Enforce peer review for all app code before deploying to production environments.
- Make sure that your app code records structured audit logs for every action performed on behalf of users, including the user identity, action type, target resource, and status.
Authentication methods
To obtain tokens for Databricks Apps, both users and service principals authenticate using standard OAuth 2.0 flows. The method depends on whether the caller is a user or an automated workload.
For workspace login (users only):
- Single sign-on (SSO): Users authenticate through your identity provider when single sign-on (SSO) is configured.
- One-time password (OTP): Users receive a temporary password if SSO isn’t configured.
For OAuth flows (apps and workloads):
- User-to-machine (U2M) OAuth: Users authenticate, and the resulting tokens enable user authorization so the app can act on behalf of the user.
- Machine-to-machine (M2M) OAuth: Service principals authenticate using client credentials or federation. These tokens underpin app authorization, where the app acts as itself instead of a user.
For instructions to call a Databricks app using token authentication, see Connect to an API Databricks app using token authentication.
Compare and combine models
Databricks Apps can use app and user authorization independently or together. These models serve different purposes and are designed to work in parallel.
Authorization model | When to use | Example use cases |
|---|---|---|
App authorization | When the app performs operations that don’t depend on the user’s identity | Writing logs, accessing shared configuration, calling external services |
User authorization | When the app needs to access resources in the context of the current user | Querying Unity Catalog data, launching compute, enforcing row-level permissions |
Both | When the app performs both shared and user-specific operations | Logging metrics with app identity, querying filtered data with user identity |