Configure Databricks on AWS sign-on from Power BI with Microsoft Entra ID
This feature is in Private Preview.
This article describes how to enroll in the Private Preview for configuring Microsoft Entra ID (formerly Azure Active Directory) as the identity provider (IdP) for single sign-on (SSO) to Databricks on AWS from Power BI.
Requirements
Before you configure SSO to Databricks on AWS from Power BI with Microsoft Entra ID, make sure you have the following:
-
Power BI version 2.124.581.0
-
A Microsoft Entra user with a valid email claim. This email claim must also be a user in your Databricks workspace.
-
Unified login enabled for your Databricks workspace.
-
Your Microsoft Entra tenant ID. See How to find your Microsoft Entra tenant ID in the Microsoft Entra documentation.
The Microsoft Entra tenant ID must match the Power BI tenant ID. To find your Power BI tenant ID, see Find your Fabric home region. Your tenant ID is the value after
ctid=in the tenant URL.
If your workspace doesn't meet the requirements, contact your Databricks representative to enroll your Microsoft Entra tenant in the Private Preview. You'll have to provide your Microsoft Entra tenant ID and your Databricks account ID.
Self-serve enrollment steps
To enroll your Microsoft Entra tenant in the Private Preview, follow the steps in SSO to Databricks with Microsoft Entra ID, but don't paste the OpenID Connect metadata document value into the OpenID issuer URL field. Instead, your OpenID issuer URL must include your Microsoft Entra tenant ID and end with a forward slash. The format must be exactly the following:
https://sts.windows.net/<tenant-id>/
Troubleshoot configuration
If the Test SSO validation step in SSO to Databricks with Microsoft Entra ID fails, verify the following:
-
The OpenID issuer URL contains your Microsoft Entra tenant ID and ends with a forward slash. For example:
https://sts.windows.net/<tenant-id>/ -
Your Microsoft Entra user has a valid email claim. This email claim must also be a user in your Databricks workspace.
noteMake sure your user email property is consistent with your User principal name property. Both properties must be members of your Databricks workspace.
You might have to configure optional claims. To do this, follow https://learn.microsoft.com/entra/identity-platform/optional-claims. Make sure you have the email claim in both id token and access token.
Users can now select the Azure Databricks connector when creating a manual connection from Power BI Desktop and specify Azure Active Directory as the authentication type to SSO to Databricks with Microsoft Entra ID.
Although the connector name is Azure Databricks, it works with Databricks on AWS. Do not select the Databricks connector.
You can also enable SSO for access to reports in the Power BI service. See the next section for details.
Enable SSO to access reports in the Power BI service
You can enable SSO so that when you publish a report to the Power BI service, users can access reports built using DirectQuery storage mode by passing their Microsoft Entra ID credentials to Databricks.
-
Publish your Power BI report from Power BI Desktop to the Power BI service.
-
Enable SSO access to the report and underlying data source.
-
Go to the underlying Databricks dataset for the report in the Power BI service, expand Data source credentials, and then click Edit credentials.
-
On the configuration dialog, select Report viewers can only access this data source with their own Power BI identities using Direct Query, and then click Sign in.
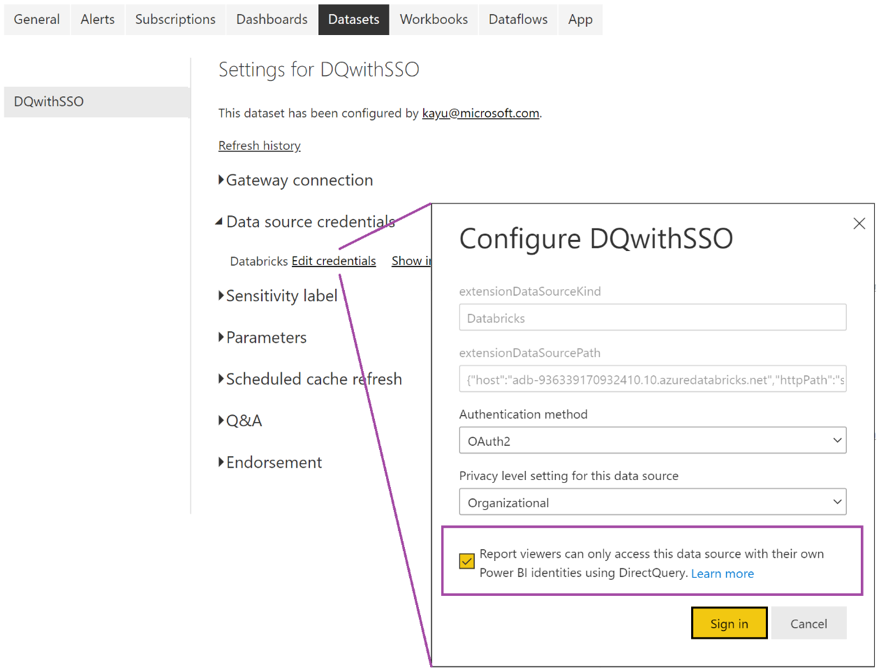
With this option selected, access to the data source is handled using DirectQuery and managed using the Microsoft Entra ID identity of the user who is accessing the report. If you don't select this option, only you, as the user who published the report, have access to the Databricks data source.
-