Manage personal access token permissions
This article describes the how to configure permissions for Databricks personal access tokens. To learn how to use credentials to authenticate to Databricks, see Authorize access to Databricks resources. To monitor and revoke personal access tokens, see Monitor and revoke personal access tokens.
Basic authentication using a Databricks username and password reached end of life on July 10, 2024. See End of life for Databricks-managed passwords.
Personal access token permissions
Workspace admins can set permissions on personal access tokens to control which users, service principals, and groups can create and use tokens. Before you can use token access control, a Databricks workspace admin must enable personal access tokens for the workspace. See Enable or disable personal access token authentication for the workspace.
A workspace user can have one of the following token permissions:
- NO PERMISSIONS: User cannot create or use personal access tokens to authenticate to the Databricks workspace.
- CAN USE: User can create a personal access token and use it to authenticate to the workspace.
- CAN MANAGE (workspace admins only):** User can manage all workspace users' personal access tokens and permission to use them. Users in the workspace
adminsgroup have this permission by default and you cannot revoke it. No other users, service principals, or groups can be granted this permission.
Databricks personal access token permissions are available only in the Premium plan or above.
This table lists the permissions required for each token-related task:
Task | NO PERMISSIONS | CAN USE | CAN MANAGE |
|---|---|---|---|
Create a token | x | x | |
Use a token for authentication | x | x | |
Revoke your own token | x | x | |
Revoke any user's or service principal's token | x | ||
List all tokens | x | ||
Modify token permissions | x |
Manage token permissions using the admin settings page
This section describes how to manage permissions using the workspace UI. You can also use the Permissions API or Databricks Terraform provider. When a user's CAN USE or CAN MANAGE permission is revoked, their tokens become unusable. If the permission is restored, the same tokens become usable again.
-
Go to the settings page.
-
Click the Advanced tab.
-
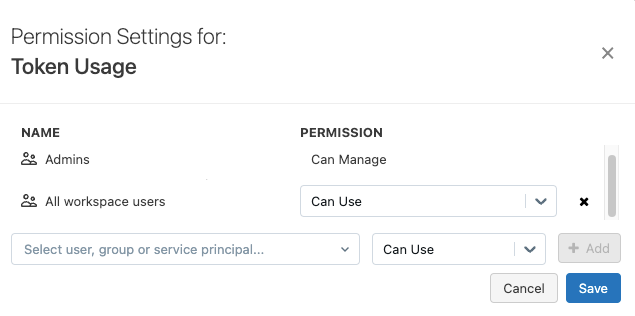
Next to Personal Access Tokens, click the Permissions button to open the token permissions editor.
-
Search for and select the user, service principal, or group and choose the permission to assign.
If the
usersgroup has the CAN USE permission and you want to apply more fine-grained access for non-admin users, remove the CAN USE permission from theusersgroup by clicking the X next to the permission drop-down menu in the users row. -
Click + Add.
-
Click Save.