Configure Inbound PrivateLink
This page covers configuration steps for inbound private connectivity between users and their Databricks workspaces. To enhance the security of your workspace's serverless implementation, you must use inbound private connectivity.
- For architectural concepts and deployment options, see PrivateLink concepts.
- For an overview of private connectivity at Databricks, see Classic compute plane networking.
- To enable classic private connectivity to Databricks, see Configure classic private connectivity to Databricks.
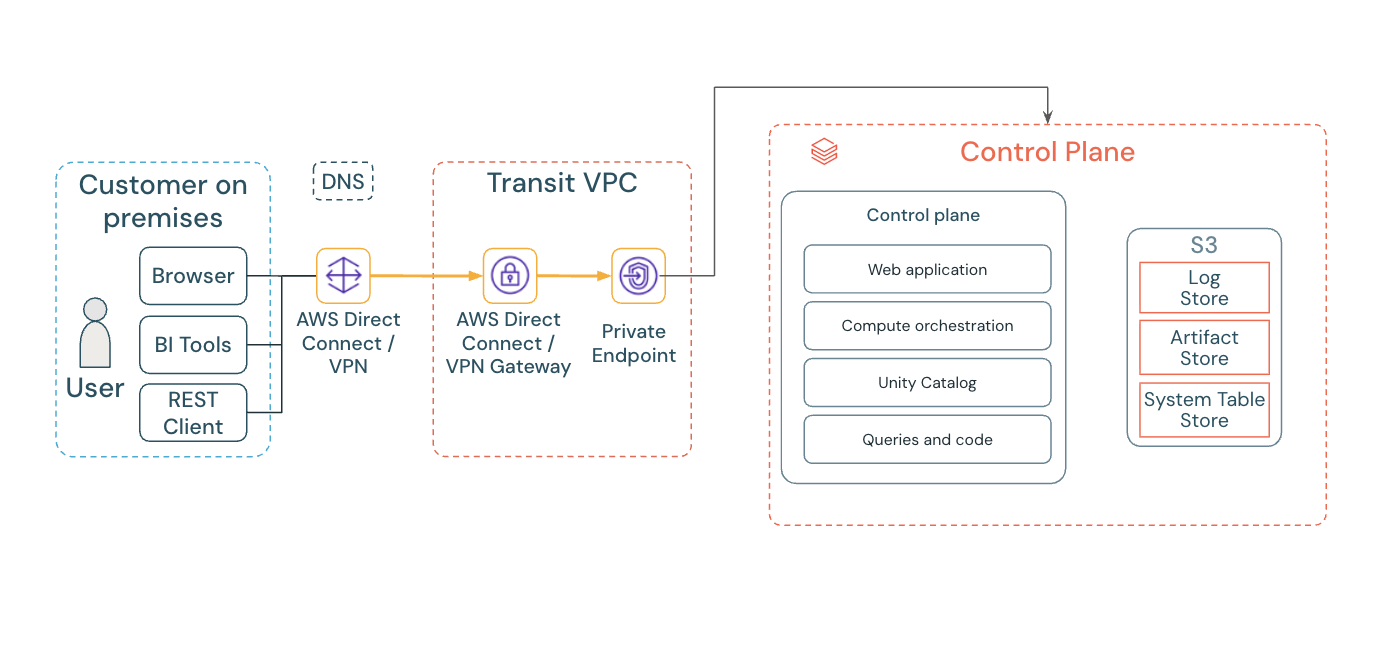
Establish secure, private connections from your AWS VPCs or on-premises networks to Databricks services using inbound PrivateLink, which routes traffic through a VPC interface endpoint instead of the public internet.
An inbound endpoint originates from your transit VPC, typically serving as the source for user web application access. This is usually a separate VPC from the workspace's compute plane VPC and can be connected to an on-premises network. If you have multiple Databricks accounts, share an inbound VPC endpoint across these accounts by registering the endpoint in each relevant Databricks account.
With inbound PrivateLink:
- Configure private access: Configure inbound PrivateLink connections to the Databricks web application, REST API, and Databricks Connect API.
- Enable private access: Configure PrivateLink when you create a new workspace or on an existing one.
- Enforce private connectivity: Configure private connectivity from users to Databricks.
Requirements
- Your Databricks account is on the Enterprise plan.
- You must have all necessary AWS permissions to set up a Databricks workspace and to create new VPC endpoints for your workspace.
- To establish an inbound PrivateLink connection for accessing the workspace from your on-premises network, connect your on-premises network to an AWS VPC using Direct Connect or VPN.
- Allow network traffic from all relevant address spaces within your local network to connect to your VPC endpoint using TCP port 443.
Step 1: Create VPC endpoints
To create inbound VPC endpoints in the AWS Management Console:
- Go to the VPC endpoints section of the AWS Management Console.
- In the upper right, set the region to the same region as your transit VPC region.
- Click Create Endpoint.
- When naming the endpoint, Databricks recommends including the region and either
workspaceorinbound, such asdatabricks-us-west-2-workspace-vpce. - Under Service Category, select Endpoint services that use NLBs and GWLBs.
- In the service name field, paste the service name. Use the table in PrivateLink VPC endpoint services to find the regional service names. Copy the one labeled Workspace (including REST API).
- Click Verify service and check that Service name verified appears in a green box. If you encounter an error that states "Service name could not be verified", verify that the regions of your VPC, subnets, and new VPC endpoint are correctly matched.
- In VPC, select your transit VPC.
- In Subnets, select a subnet.
- In the Security groups section, select a security group that allows inbound traffic on port 443 from the IP ranges that need to access the workspace.
- Click Create endpoint.
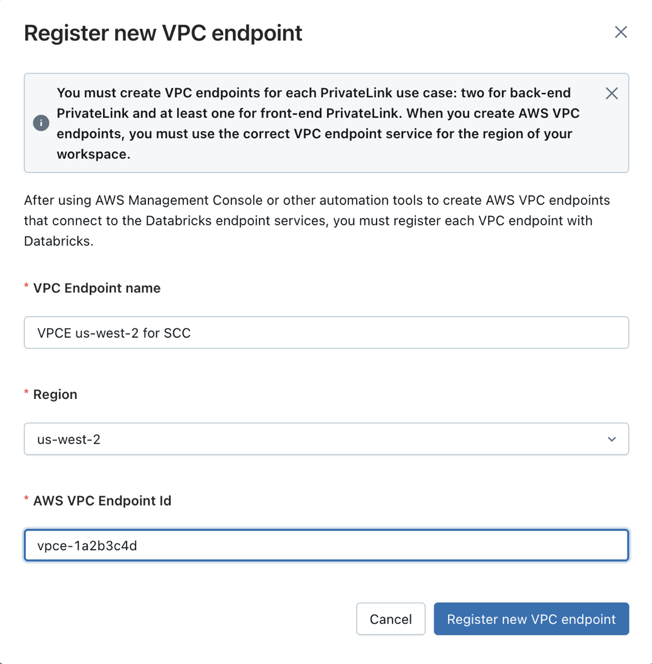
Step 2: Register VPC endpoints
After you create your VPC endpoints in the AWS Management Console, register them with Databricks. You can't update a network configuration after it has been created. Follow these steps to register your VPC endpoints:
-
Go to the Databricks account console.
-
Click Cloud resources in the sidebar.
-
Select Network.
-
Click VPC endpoint registrations from the vertical navigation.
-
Click Register a VPC endpoint.
-
Enter a descriptive name for your VPC endpoint registration.
- A naming convention that includes the region and purpose is recommended, such as
VPCE us-west-2 for REST.
- A naming convention that includes the region and purpose is recommended, such as
-
Select the appropriate region. The region must match both your workspace region and the region of the AWS VPC endpoints that you're registering.
-
Paste the AWS VPC endpoint ID in the AWS VPC endpoint ID field.
-
Click Register new VPC endpoint.
If you have multiple workspaces that share the same customer-managed VPC, you can share AWS VPC endpoints among them. For multiple Databricks accounts, register the AWS VPC endpoint in each account.
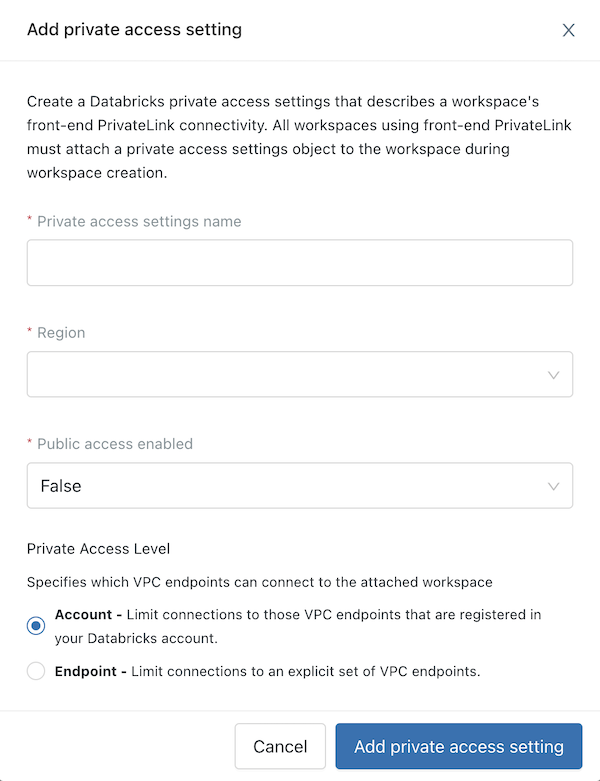
Step 3: Create private access settings
Private access settings describe your workspace's PrivateLink connectivity and are required to enable private connectivity. To use PrivateLink, you must attach a private access settings object when you create your workspace. Follow these steps to create your private access settings:
-
In the account console, click Security in the sidebar.
-
Click Private access settings in the sidebar.
-
Click Add private access settings.
-
Enter a name for your new private access settings object.
-
Select a region that matches your workspace region.
-
Configure the Public access enabled field:
- False (default): The inbound connection is accessible exclusively through PrivateLink, blocking public internet access.
- True: The inbound connection is accessible through both PrivateLink and the public internet.
tipDatabricks recommends starting with True while testing your DNS configuration. After DNS is finalized and confirmed working, change to False during a maintenance window to enforce exclusive private connectivity. Note that the private access settings object cannot be modified after creation, so you'll need to create a new PAS object and update your workspace configuration.
-
Select a Private Access Level:
- Account: Limit connections to VPC endpoints registered in your Databricks account.
- Endpoint: Limit connections to an explicit set of VPC endpoints. Include your inbound VPC endpoint registration.
-
Click Add private access settings.
Step 4: Create your workspace with PrivateLink objects
To complete this step, your workspace must already be using a customer-managed VPC and secure cluster connectivity.
-
See Create a classic workspace to create a workspace. Refer to that page for guidance on workspace fields such as workspace URL, region, Unity Catalog, credential configurations, and storage configurations. Don't click the Save button yet.
-
Click Advanced configurations to view additional fields.
-
In the PrivateLink dropdown, choose the name of the private access settings object that you created in previous steps.
-
Click Save.
-
After you create or update a workspace, wait until it is available before you use or create clusters.
The workspace status remains
RUNNINGand the VPC change happens immediately. However, you can't use or create clusters for another 20 minutes. If you create or use clusters before this interval ends, clusters might fail to launch or cause other unexpected behavior.
Step 5: Configure DNS for inbound PrivateLink
After creating your inbound VPC endpoint, configure DNS to route user requests through your private network to the VPC endpoint's private IP address.
For comprehensive DNS configuration instructions, including Route 53 setup, conditional forwarding patterns, and troubleshooting guidance, see Configure DNS for AWS inbound PrivateLink.
Quick verification
After configuring DNS, verify that your workspace URL resolves to a private IP address:
nslookup myworkspace.cloud.databricks.com
Expected output showing resolution through the privatelink subdomain:
myworkspace.cloud.databricks.com canonical name = sydney.privatelink.cloud.databricks.com
Name: sydney.privatelink.cloud.databricks.com
Address: 10.176.10.182
The workspace URL should resolve to the private IP address of your inbound VPC endpoint, not a public IP address.
Step 6: Configure inbound PrivateLink with unified login
Unified login with inbound PrivateLink is in Private Preview. You must contact your Databricks account team to request access to this preview. For more information on unified login, see Enable unified login.
If your users have access to the public internet, this step is not required.
When a user logs in to a workspace where unified login is enabled, the system redirects them to accounts.cloud.databricks.com in the authentication flow. To use unified login with a workspace where inbound PrivateLink is enabled and the user has no access to the public internet, follow these steps to configure your identity provider and internal DNS.
Authorize the PrivateLink redirect URI in your identity provider
- As an account admin, log in to the account console.
- In the sidebar, click Settings.
- Click the Authentication tab.
- Next to Authentication, click Manage.
- Choose Single sign-on with my identity provider.
- Click Continue.
- Copy the value in the Databricks Redirect URL field.
- Replace
accountswithaccounts-pl-authto get the Databricks PrivateLink Redirect URI. - Go to your identity provider.
- Add the Databricks PrivateLink Redirect URI as an additional redirect URL. If you configure SSO using SAML, also add the Databricks PrivateLink Redirect URI as an additional entity ID.
If you have both PrivateLink and non-PrivateLink workspaces in your account, do not remove the Databricks Redirect URL with account from your identity provider redirect URLs.
Set up a private hosted zone for your transit VPC
Perform the following configuration in your transit VPC to verify that the Databricks PrivateLink Redirect URI maps to the VPC endpoint private IP address for your workspace VPC endpoint.
- From your transit VPC, use the
nslookupUnix command-line tool to get the DNS resolution using your workspace URL. See the example in Step 5: Configure DNS for inbound PrivateLink. - Copy the control plane instance URL of your PrivateLink workspace. The control plane instance URL is in the format
<region>.privatelink.cloud.databricks.com. - In your transit VPC, create a private hosted zone with the domain name
privatelink.cloud.databricks.com. - Add a CNAME record that resolves
accounts-pl-auth.privatelink.cloud.databricks.comto your control plane instance URL. - Test the configuration by accessing the Databricks PrivateLink Redirect URI from your transit VPC.